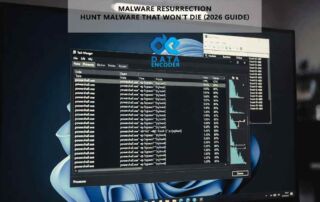
Crypter is a software tool that encrypts executable files, making them more difficult to detect by antivirus programs. Crypters like the Crypter data encoder work by encrypting the code of the executable file, making it more difficult for antivirus software to analyze and detect the presence of malicious code.
The use of crypters is becoming increasingly common among cybercriminals, who use them to deliver malware payloads and evade detection by security software.
Crypter advantages
One of the key advantages of using a crypter is that it can make malware and other malicious code more difficult to detect by antivirus software. It can make it easier for attackers to deliver their payloads and infect systems with malware.
Crypters can play a significant role in cyber attacks, particularly in the delivery of malware payloads. Malware developers often use crypters to encrypt their malicious code, making it more difficult for antivirus software to detect and analyze.
Using a crypter, attackers can create malware that is more difficult to detect and block by the security software, increasing the likelihood of their attack’s success. Crypters can also be used to obfuscate other attack techniques, such as process hollowing and DLL injection, making them more difficult for security software to detect.
Crypter Attacks
In addition to delivering malware, Crypters has the potential to steal sensitive information from victims by encrypting the code of a keylogger. Pure crypters make detecting and blocking the activity harder for security software. It allows attackers to capture their victims’ sensitive information, such as login credentials, financial data, and personal information.
Crypters can also be used with other attack techniques, such as social engineering, to deceive victims into downloading and executing malicious files. By using a convincing phishing email or a different tactic, attackers can trick victims into downloading and running a crypter-encrypted malware payload, increasing the likelihood of a successful attack.
In summary, crypters can play a significant role in cyber attacks by allowing attackers to deliver malware payloads and steal sensitive information from victims.
Runtime encryption software is a type of software that secures data during encrypted files run on the system. So, it is named FUD Runtime when it can stay FUD or fully undetectable. Note fud crypter cracked version like Data Encoder Crypter Cracked can’t help you.
Price will determine by various factors. Firstly FUD results in Runtime and Scantime. Therefore, online support. Data Encoder crypter working from 2024 can secure your data and work with top RAT 2024 with secure connections.