Prevent Windows Defender from flagging clean apps with Resolve Antivirus False Positives. You shouldn’t lose customers for false flags.
Data Encoder is a false positive resolution service built for independent software vendors (ISVs), enterprise developers, and security teams who need their legitimate applications to pass modern antivirus scans—without triggering unwarranted alerts from Windows Defender, Kaspersky, Bitdefender, and others.
We don’t “trick” security software. Instead, we adjust non-functional traits in your executable—like metadata structure, code layout, and startup behavior—to align with patterns recognized as safe by major AV engines.
This isn’t about hiding code. It’s about ensuring your software is seen for what it truly is: clean, safe, and trustworthy.
Why Do Antivirus Engines Flag Clean Software?
Modern antivirus systems use behavioral heuristics, machine learning models, and generic signatures to detect unknown threats. While effective against malware 2026, these systems often misclassify legitimate software that:
- Writes to the registry or file system during setup
- Communicates over the network (e.g., for license validation or telemetry)
- Uses packed or compressed .NET assemblies
- Runs background services or self-updaters
According to Antivirus Comparatives’ 2025 report, over 12% of business applications triggered at least one false positive during routine scans. For developers, this means:
- Users deleting your app before first launch
- Enterprise IT blocking deployment
- Rejection from software marketplaces like Microsoft Store
- Increased support tickets about “virus warnings”
Data Encoder helps you resolve these misclassifications at the binary level—without changing your application’s functionality.
Why Choose Data Encoder Crypter?
Full Compatibility
Supports .NET Framework, .NET Core, and native Win32/Win64 applications. Fully tested on Windows 10 (22H2+) and Windows 11 (23H2+), including ARM64.
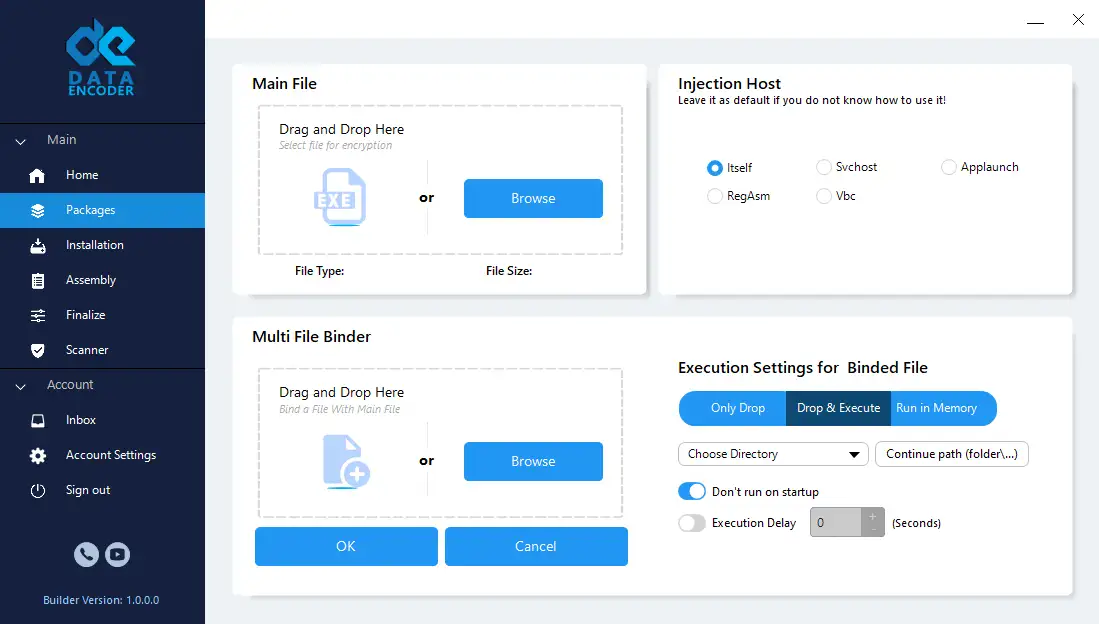
Multi-File Binding (Optional)
Bundle DLLs, config files, or assets into a single executable—without triggering packer-based heuristics. Ideal for portable or self-contained deployments.
Scantime + Runtime Protection
Reduces false flags both during initial scan and while your app is running—critical for applications with background processes.
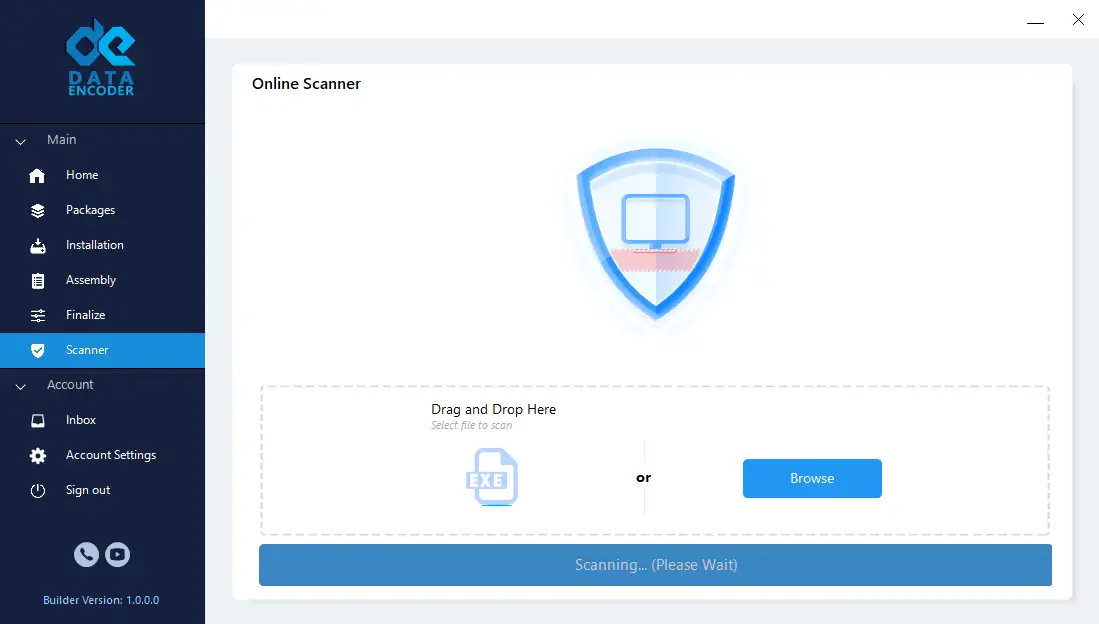
Integrated Verification Dashboard
Upload your protected executable to scan against 30+ antivirus engines in real time. Includes behavioral sandbox reports and compatibility scoring to fix AV False Positives.
Custom Profile Options
Choose between shared and private processing profiles—each tuned to balance cost, update frequency, and detection resilience.
No Performance Penalty
Unlike heavy packers, Data Encoder adds negligible overhead. Startup time remains within 2–5% of the original binary.
How AV to fix False Positives: A Developer-First Service
Data Encoder is not a packer, crypter, or generic obfuscator. It’s a false positive resolution engine that analyzes your executable and applies precision adjustments to reduce heuristic noise. It will resolve AV False Positives.
The process includes:
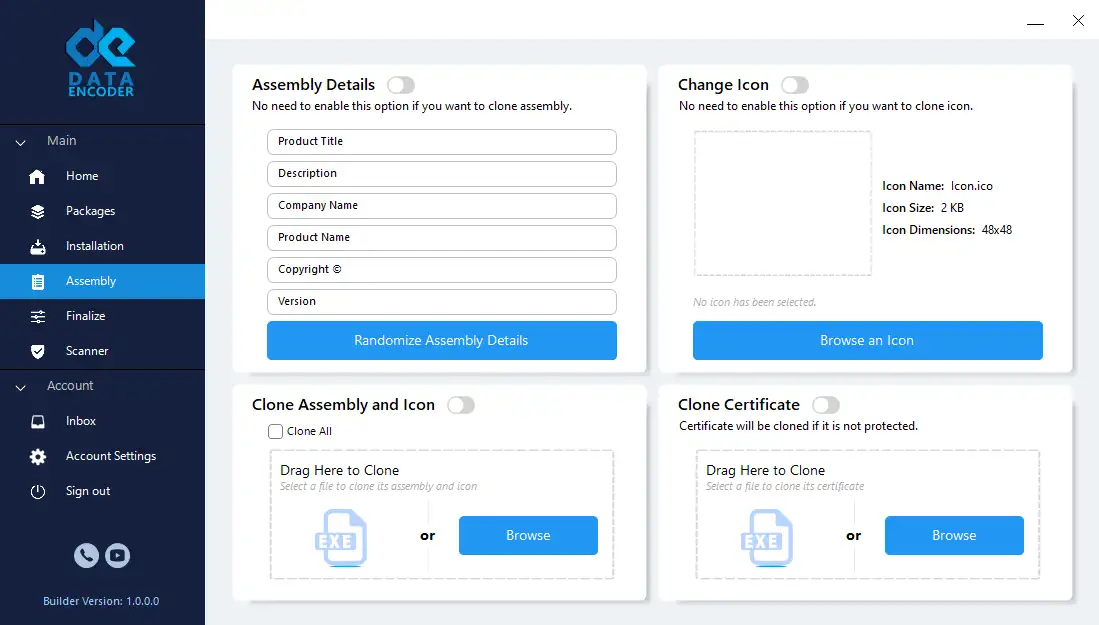
- Binary Reshaping: Modifies non-essential PE header fields and metadata to match clean software profiles
- Code Layout Optimization: Reorganizes instruction sequences to avoid patterns associated with malicious packers—without altering logic
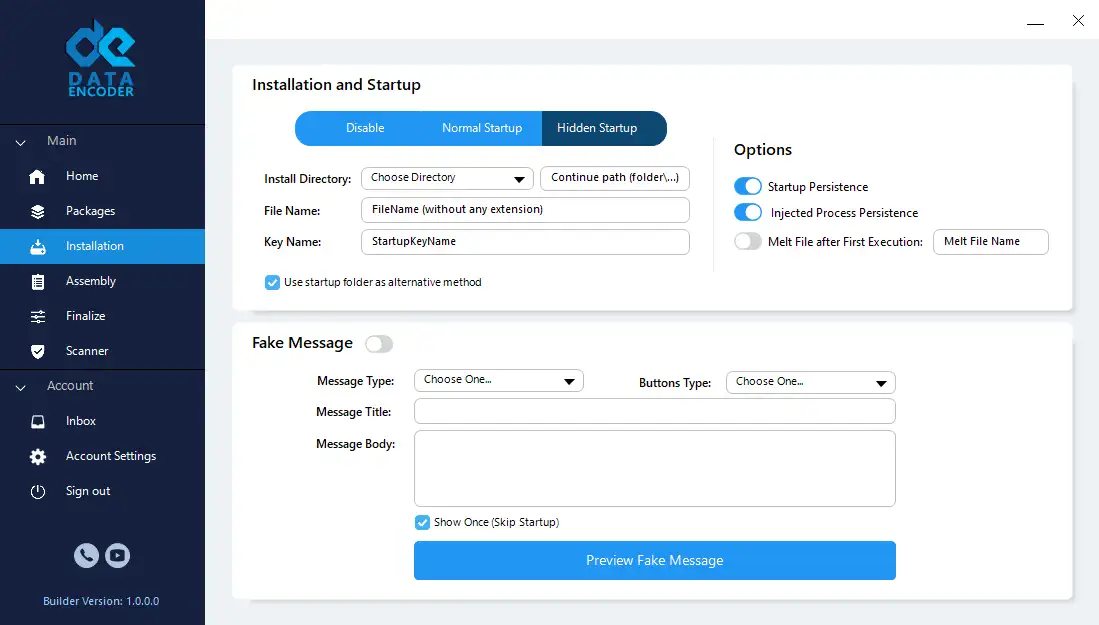
- Startup Behavior Normalization: Ensures installation and auto-start routines mimic those used by trusted software (e.g., Slack, Zoom, Adobe)
- Multi-File Integration (Optional): Bundles DLLs, configs, or assets into a single executable—ideal for portable or self-contained apps
All changes are fully reversible during development and add negligible performance overhead (<5% startup impact). We suggest reading AV comparisons for more details
“Our service is exclusively for developers distributing non-malicious software. Use on deceptive, unauthorized, or harmful code violates our terms.”
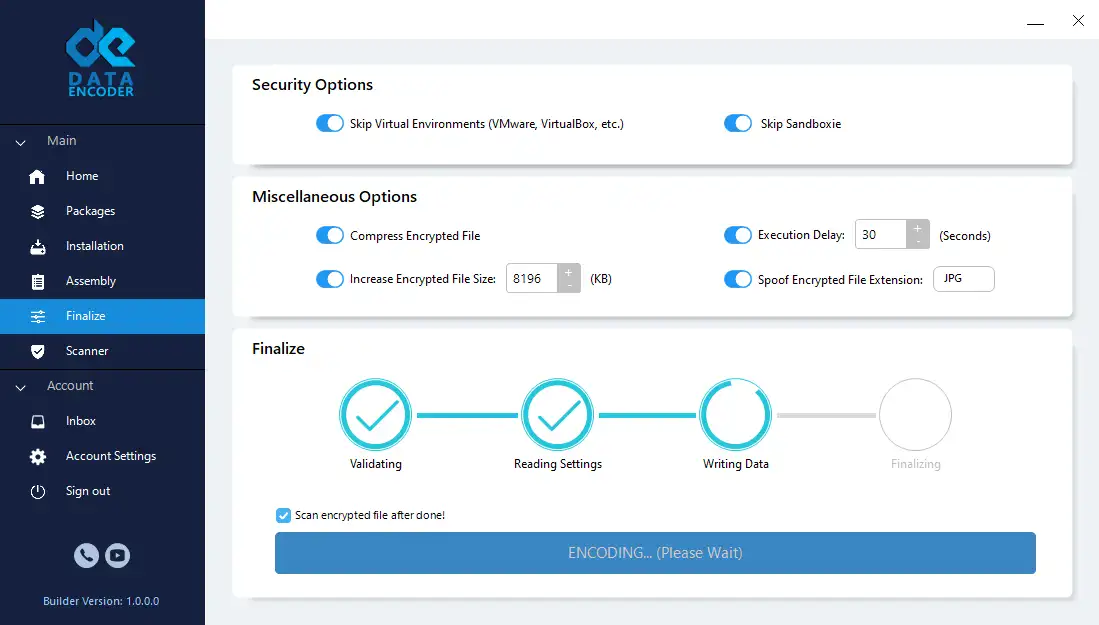
Data Encoder Screenshots
Select your service
Public Plan – Bronze
For 45 Days
- ✓ All features available
- ✓ Unlimited Encryption
- ✓ Shared Results
- ✓ Standard Support
- ✓ Free updates
- ✓ 2 Reset HWID (Hardware ID)
Private Package #1
For 45 Days
- ✓Advanced Guaranty (Ask for details)
- ✓ Unlimited Encryption
- ✓ Dedicated binary profile in your hands
- ✓ 5 Free updates
- ✓ Access to Public Plan
- ✓ False Positive Resolution Assurance
- ✓ Priority support + remote demo sessions
- ✓ 2 reset HWID (Hardware ID)
Ethical Boundaries: What We Support (and What We Don’t)
Data Encoder is used by:
- Indie game studios
- SaaS companies with desktop clients
- Internal IT teams building admin utilities
- Blue team & Red team professionals under authorized engagements
We do not support:
- Obfuscation of malware, ransomware, stealers, or RATs
- Deployment to systems without user consent
- Attempts to disable or interfere with security software
All users must certify their software’s legitimacy before access is granted.
Why No Public Trial?
Because our resolution models are adaptive and fingerprint-sensitive, a public trial would expose patterns that could degrade effectiveness for all legitimate users.
Instead, we offer:
- A free diagnostic scan: Submit your EXE for a false positive risk assessment
- A live demo session: See the process via screen share—no download required
- A 10-day refund guarantee for Advanced private package if false positives persist
Ready to Ship Without False Alarms?
Over 850 developers have used Data Encoder to:
- Pass enterprise security reviews
- Reduce user complaints about “virus warnings”
- Successfully distribute software via trusted channels
You can:
- Submit your EXE for a free compatibility report
- Schedule a 10-minute demo
- Start with a shared plan and upgrade to private when ready
[Get Started – Resolve False Positives in Minutes]