Stealer is one of the malware types that work in the back end of your system for a short time. The duty of stealer malware is to identify windows software and web browsers. Then copy any info such as login credentials, financial credentials, system configuration details, system IP, most crypto wallet, VPN account, FTP account, location data, and any susceptible data needs to log in with username and password. Read more about spyware, stealer price, and top stealer 2024.
The best stealer 2024 has unique features with hidden access methods. Some malware hasn’t encrypted form, so hackers try to employ malware crypter to encrypt the data. Finally, forward encrypted information back to the hackers’ server.
Attackers use advanced methods like Fast Flux DNS or DNS tunneling with top Stealer for hiding IP and DNS.
Basic information about Stealer malware
- Russian developers made the best Stealer malware on the darknet. Therefore, most of this spyware can not be used by people in the Commonwealth of the Independent States or CIS.
- The Microsoft report shows North Korea and Russia nations are active Stealer malware actors in 2024 to recover their income by stealing cryptocurrency. Read the cyber attaks in 2023 too.
- Based on the malware threats trackers, the top Stealer 2023 made during Covid 19 pandemic. Also, some spyware released rebuilt versions During this period.
- This hack tool is produced for beginner and professional users. Therefore, many unfamiliar with hacking can easily use this malware.
- There are different types of stealers. Some are in MaaS or Malware as a Service or Windows-based connection.
- The Stealer is an individual part of Remote Access Trojans that works primarily on the clipboards. It is named Clipper software too. Some stealers replace the wallet address with hacker defined address. So victims don’t know the attacker’s access and don’t check the copied wallet address. Do you know how make FUD RAT? read our blog posts for more information.
- Malware analysis shows attackers use Telegram, Google driver, Google Ads, Discord server, and private servers for communication and spreading methods.
- Attackers use FUD crypter 2023 to secure the data and bypass antivirus. (Read the links if you don’t know about how crypter works) . You can watch how to bypass Windows Defender now.
- It formats were detected as EXE, PDF, DOC, ZIP, RAR, ACE, and ISO files.
Top spyware Malware 2024
You need to know the top Stealer malware 2024 to find the best way to protect your sensitive data. Malware use updated methods to infect your system. We recommend watching bypass antivirus videos.
Anyone can find these malware on Google and Github or buy it straight from the coder onTelegram.
Microsoft report (June 2021) detects these top spyware.
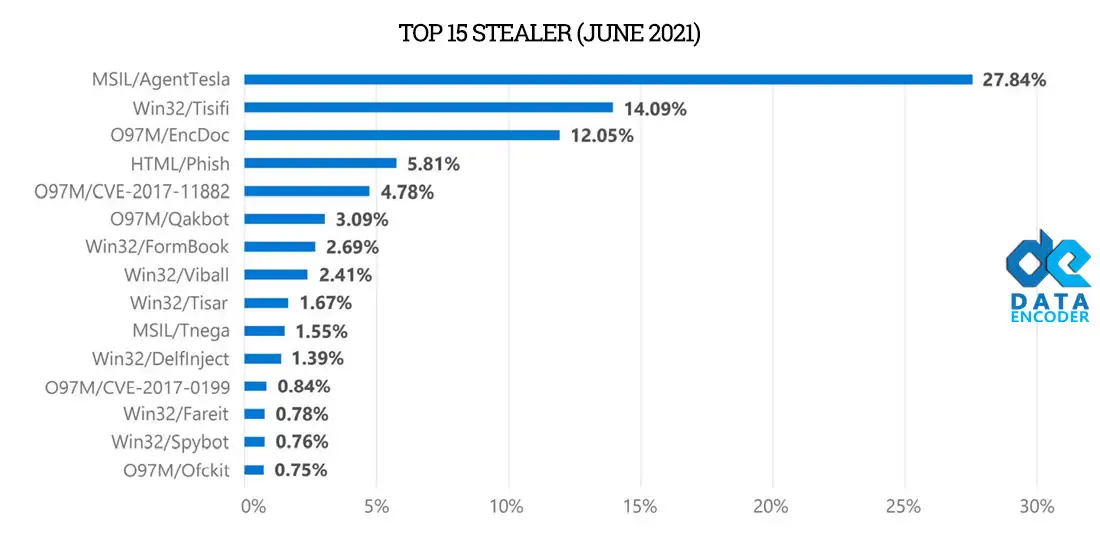
Microsoft Report for Stealer Malware
But the most common Stealer malware in use in 2023 is these. In short, some of these Spywares are RAT Remote Access Trojans 2022, Ransomware, or Exploit, but we put them on the top list because their most used goal is stealing.
The top Stealer Malware 2023
As you can see, the most common Stealer used in 2023 is Redline, Raccon, Emotet, Formbook, and Agent Tesla. All statistics are in percent.
In short, the above price stealer starts from $100. and attackers sell credential details for $1 per 1000 on the darknet.
As results shows, most spyware will detect by antivirus. So attackers use encrypted methods to eliminate antivirus and security program layers. Already, they are using crypter 2024 to encrypt the stolen data. We will explain thoroughly about malware crypter in the following articles. But for now, it is different from crypter software.
Do you want to find the malware? If you suspect that your system is infected with malware or not, install anti-malware on your system. The best tool to remove malware is to use Windows Defender. If you are semi-professional, you can check the suspicious behavior of system processes.
Between various types of malware Trojan, Viruses, Worms, Spyware, ransomware and extortion, Hidden miner, RAT Remote Access Trojans, Botnets, Stealer, Keylogger, Hidden Miner, and malware crypter. The most common malware kits in 2022 are RAT remote access trojans and Botnets. The type of use varies depending on the time and place of each malware. For example, in the Russian invasion of Ukraine, the use of malware has changed.
Malware is often referred to as short-term “Malicious Software.” Malware means malicious programs, applications, or codes that are harmful to the technical devices generally connected to the Internet. The attacker with malware can get hidden access to the victim’s system.
The price of Stealer
Stealer malware prices start from $70 up to $1200. Stealer price depends on options, updates, and support in monthly or Pro versions. Many Stealer coders sell malware on Telegram. Users can buy stealers from Bitcoin, Ethereum, and more.
As told before, attackers use free fud crypter to bypass any detections. So newbies start this malware with low price or bots 2023.
Updated list of Stealer 2000-2024
We create a list of the last Stealer 2000-2020 and update it for more information. This list helps you know the top Stealer better.
This list was updated on 05/15/2024. Share your experience with these tools with us.
| Stealer List 2024 | |
|---|---|
| Redline | Bloody |
| formbook | X-Files |
| Lokibot | Strong Brain |
| Vidar | Sorano |
| Ave maria | Mystery |
| Azorult | TRON |
| Danabot | Right Stealer |
| Pony (Fareit) | Heleks |
| Qbot | Ginzo |
| Trickbot | EXO-STUB |
| Icedid | Lucky |
| Gootkit | Taurus |
| Dridex | Crypto Wares |
| Zloader | Collector |
| Predator the thief | Silex |
| Gozi | Armageddon |
| Tinba | Telerax |
| Cridex | Istealer |
| Cryware | Kpot |
| GameOverZeus | Eternity |
| Raccon | Nosu |
| Rhadamanthys | Emotet |
| SpyEye | Ursnif |
| CryptoShuffler | FakeWallet |
| ClipboardWalletHijacker | Evil Clippy |
| Rilide | Meduza |
| Bandit | RedEnergy |
| Wise Remote | Sapphire |
| Stealer List 2024 | |
|---|---|
| SolarMarker | Lumma |
| TimbreStealer | Stealc |
| DarkGate | ViperSoftX |
| ClipBanker |
Briefly, some stealers use loader 2023 to keep the backdoor to the victim’s system.
How to protect your bank account or crypto wallet from Spyware?
As mentioned before, the main goal of spyware is your sensitive data like your bank account or cryptocurrency wallet. So it copies your credentials with your system details like IP and uses them to bypass the Two Factor Authentication or 2FA layer. As you see, the stealer price is low for attackers. So we need to be careful about its attacks.
So, how to protect your data and stand against attackers?
It is simple to follow these steps but not easy to find the malware if you aren’t a professional. Therefore just follow these steps as soon as possible.
Do you have any experience with Stealer? Do you have any idea how to remove it? Please share it here.
Do you need to know about best miner 2021? We write a list for you. Join our crypter channel for more information.
