Do you know remote access trojans 2022-2023? The last decade has generated many remote access tools or RAT trojan. Based on research, over 300 RAT Windows with different options were released as free RAT tools or paid versions.
Currently, Most of these Windows RAT programs are discontinued, cracked, or vanished from the market and darknet. Most users try to download the RAT tool for hacking purposes. In this article, Let’s review some of the most used and best of them and introduce the list of the top RAT remote access tool 2022-2023.
Brief introduction of RAT tool (Remote Access Trojans)
A RAT trojan (remote access trojan) is a malware generator. This program gives the administrator access to the victim system. In short, some remote access tools have HVNC (Hidden Virtual Network Computing) option.Read more about what is RAT trojan software.
So, the victim cannot see the hacker’s activity. See how to make FUD RAT.
RAT pc gives these accesses to the hacker
- All your system data is on your hard disk.
- All your windows system settings.
- All password and credential information such as financial, emails, social media, etc.
- remote access trojan 2022-2023 will access Webcam, Microphone, etc. too.
How does RAT remote access tool 2022-2023 works?
RAT remote access tool or RAT pc has multi options to bypass antivirus detections. But, the behavior and performance of antivirus and security programs in 2022 -2023 have greatly improved.
Briefly, Crypter software 2022 encrypts and secures your data besides the antivirus. So find a crypter for RAT now to make a secure standard connection. Also, attackers using crypter clone code signing certificate for longer RAT FUD resluts.
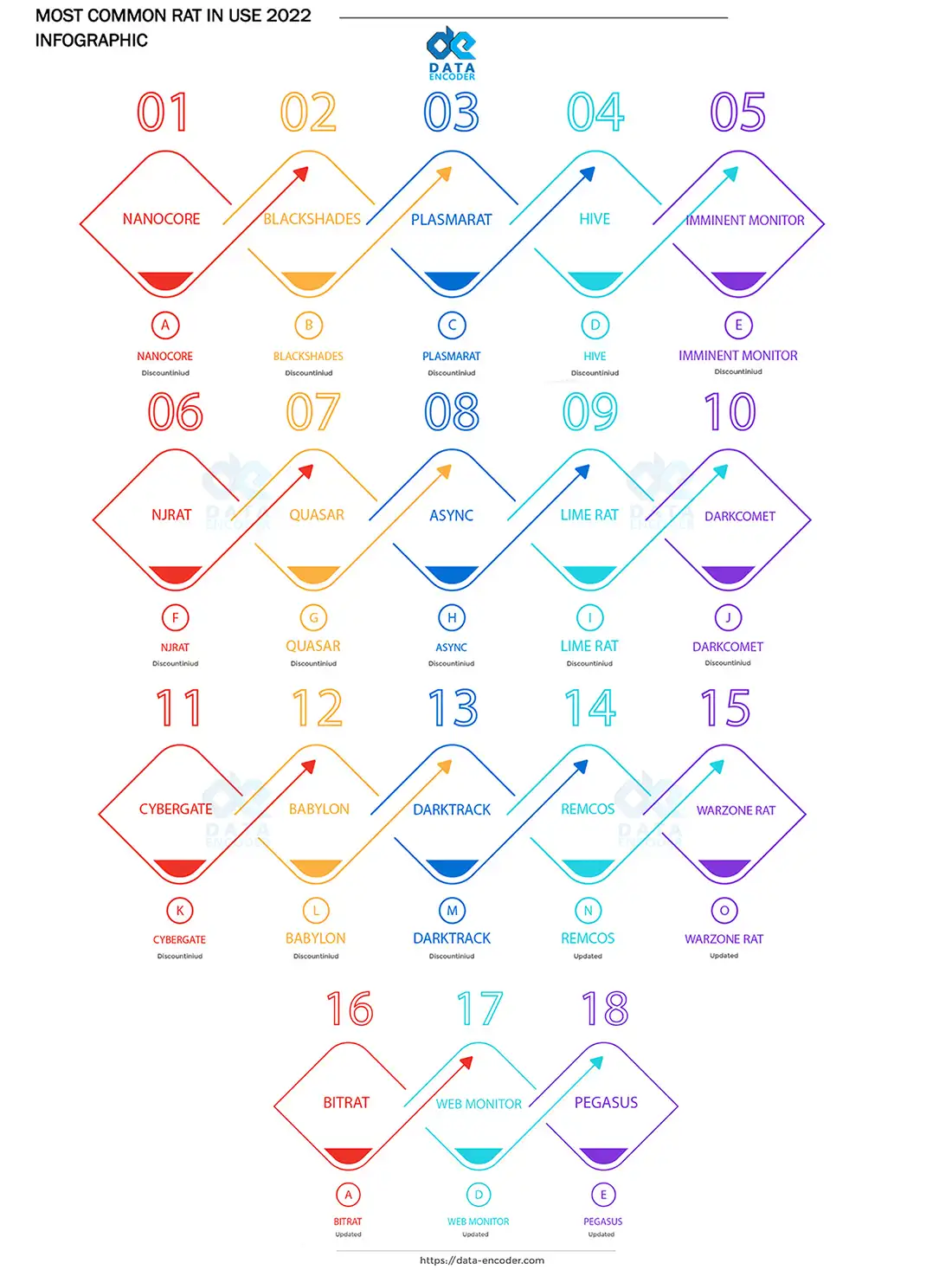
List of top RAT Trojan 2000-2022 based on user experience
Truthfully, We try to collect a list of the most used and best RAT tool from 2000 – 2022. Also, we combine some data about the status of RAT Windows activity, free RAT trojan 2022-2023, or paid type.
Please read the top Remote Access Trojan (RAT) of 2021too, if you want to know more about RAT trojans.
Notice the list of top Remote access Trojan RAT 2000 – 2020 based on user reviews and many remote access tools. Also, we have removed most of the RAT remote access trojan due to the lack of sufficient information about them.
However, insufficient information about many of the list software has caused us can’t write information about them. Also, you can’ find most Remote access tools hacks on Google, and don’t search for Remote access Trojan downloads because it is illegal.
Note most these remote software compatible with the best crypter 2023.
Help us to update the list If you know other remote access tools.
Last Update: 09/09/2023
Most Common RAT Trojan In Use 2022-2023
The main point is RAT hacking 2022-2023 needs to update. Otherwise, it can’t be dangerous for you. We recommend watching bypass antivirus videos.
So, most free remote access trojans cannot bypass antivirus too. But some of the paid remote access trojans can bypass it. But remember that the latest updated Windows RAT on the market cannot bypass the antivirus.
Notice you have to use FUD crypter 2022 besides the antivirus to stand against attacks.
Then, you need to know how to make a file FUD with crypter. Research shows antivirus will have an issue with malware and crypter software 2022.
So crypter will help you to secure your data by encrypting the system.
In short, based on this research, the most common RAT trojan in use in 2022 free versions are Async, Quasar, Lime Rat, NanoCore, and Remcos.
Jion our crypter channel for more information.
Also, The top RAT pc 2022 paid versions are Warzone RAT, Web Monitor, and BitRat (recently back door reported).
Although, in the below list, you can see the other best remote access Trojan 2022 (free, paid, and cracked RAT).
Watch bypassing Windows Defender videos and learn how to make FUD RAT with FUD crypter 2023 for more details.
The listed RATs are currently active, but some may have received updates with new features and improved capabilities. Cyber attackers constantly enhance their tools to evade detection and make them more effective. The RATs may have changed over time.
Determining the most dangerous RATs is challenging as it depends on the target and the attacker’s intentions. However, advanced RATs like AlienSpy, Gh0st, and TrikSpy are known to compromise a system effectively. They can steal sensitive information, install other malware, and control the victim’s device. The threat level depends on the attacker’s ability to exploit vulnerabilities and bypass security measures.
Note that law enforcement or security researchers may have taken down some RATs, but their code or similar tools may still be in use. The cyber-security threat landscape is constantly changing.
This list is just a sample, and the names and versions of remote access trojan may vary. New RATs are continuously being developed, and existing RATs are being modified, so the list may not always be up to date. The best defense against RATs and other forms of malware is to stay informed and follow good security practices.
These remote access trojan 2022-2023 are dangerous due to their advanced capabilities and ability to evade detection and bypass security measures. They have been involved in several high-profile cyber attacks and are known for stealing sensitive information and controlling the victim’s device remotely. Protect yourself by staying informed and following good security practices.
The Convergence of Malware and RATs:
Malware creators have recognized the potential power of RATs and have incorporated them into their malicious code to enhance the capabilities of their attacks. Here’s how malware uses RATs to amplify their impact:
1. Persistent Access: Malware strains that incorporate free RAT functionality can establish a persistent presence on a compromised system. Even if the initial malware is detected and removed, the RAT can remain dormant, allowing attackers to regain control later.
2. Data Exfiltration: RAT remote access tool are skilled at discreetly collecting sensitive data, such as login credentials, financial information, and personal files. Malware can employ RATs to steal this data and send it back to the attackers’ command and control servers.
3. Lateral Movement: Some remote access trojans facilitate lateral movement within a network. Malware can use RATs to traverse a compromised network, hopping from one system to another, seeking valuable targets, and expanding the scope of the breach.
4. Polymorphic Capabilities: Malware authors often equip RATs with polymorphic capabilities, allowing them to change their code structure to evade signature-based detection mechanisms. This makes the malware more challenging to identify and mitigate.
5. Covert Reconnaissance: RATs are adept at gathering information about the infected system, including its hardware configuration and software environment. Malware can leverage this reconnaissance to tailor its malicious actions for maximum impact.
Case Studies:
To illustrate the synergy between malware and best rat tool, consider the following case studies:
1. Banking Trojans: Banking Trojans like Emotet and TrickBot often include RAT functionality to assist in stealing banking credentials. RATs enable these Trojans to access sensitive financial data, initiate fraudulent transactions, and maintain control over infected systems.
2. Ransomware: Ransomware variants like Ryuk and Maze have incorporated remote access trojans to aid in lateral movement and data exfiltration before encrypting files and demanding ransoms. This dual-pronged approach increases the potential harm inflicted on victims.
3. Advanced Persistent Threats (APTs): Nation-state-sponsored APT groups frequently employ RATs as part of their sophisticated campaigns. These RATs facilitate espionage by providing remote access to targeted organizations, enabling the theft of valuable intellectual property and sensitive government data.
The top RAT Windows 2022-2023 Infographics
Finally, In this section, we have tried to visualize the list of RAT trojan 2022 and have prepared the following infographic. You can see the best RAT for crypter here.
Remote access Trojan Sources
Everyone can download RAT remote access trojan 2022-2023 on Google. Free RAT software such as Quasar RAT, Async, njRAT, and Remcos free versions are available on forums too. We recommend reading how to Find, Download or Buy RAT Software. You can find these tools from sources like Social Media, Hacking forums, Darknet, official coder’s website, etc.
Suppose you want to know how to use RAT software. It is so simple that any RAT has a builder option, and it gives the payload after clicking. Any free RAT software is compatible with the best encryption software.
How stand against RAT pc?
The only way besides the antivirus is crypter software. You can encrypt all your data with FUD crypter and keep them safe from any malware and unwanted access such as Stealer. We have written numerous articles on malware and how to deal with them. Be sure to follow the tips and steps to deal with them. Also, if your system is infected with malware, follow the cleaning steps.
What are your solutions? Do you have any tips and tricks or remote access trojan 2022-2023 that we didn’t mention in this post?
Crypter Compatibility
Cyber-attacks in Coronavirus disease years (COVID-19) have increasingly infected many systems worldwide. Therefore, you will need crypter software. The crypter encrypts your files, preventing hackers from quickly accessing your data. See the last cyber attacks in 2023.
In short, you can find a free crypter and download it, but it won’t help you anymore. your tools must be compatible with ceypter software. the malware code needs to be encrypted or obfuscated in a way that is compatible with the crypter software. This is typically done to avoid detection by antivirus software and other security measures.
It would help if you had pure private crypter to can stand against last exploits and malware. We suggest watching bypass Avast video.
You can read our blog posts if you don’t know how crypter works. Also, you can make your own crypter.




PEGASUS is now compatible with all crypters.
Yes it is for now
Is nanocore compatible with the crypter?
Most crypter compatible with it
Can I get a totally free rat and crypter?
We don’t have any RAT tool
some should help me on were to get Nancore or Pegasus. Thanks in advance.
Watch our videos
please is data encoder compatibke with loki stealer
Nice
Thx
What’s wrong with these stats? Why would the discontinued, ancient, closed-source DarkComet be among top 10 most used in 2022? Madness. And the top five are all closed-source afaik, even if less ancient than DarkComet. There are nice leaked or open source RATs, why would old, closed, dead stuff be among top used? Mindboggling.
These statistics are categorized based on the latest major antivirus reports.
The core of some of these RATs has been used as new remote access, so it is still considered as a family of each RAT in the antivirus reports.