- Introduction: The Unending Cybersecurity Arms Race – Understanding Antivirus Evasion Techniques
- Chapter 1: The Dawn of Evasion – Obfuscation, Stealth, and the Seeds of Code Transformation
- 1.1 The Advent of Polymorphism: A Shifting Disguise in AV Evasion
- 1.2 Embracing Stealth: Hiding in Plain Sight from Antivirus
- 1.3 Advanced Metamorphic Code Techniques: Deep Dive into Detection Challenges
- 1.3.1 The Intricacies of Metamorphic Engines and Their Evasion Power
- 1.4 Entry Point Obscurity (EPO): A Classic Misdirection Tactic
- Chapter 2: Antivirus Countermeasures – The Rise of Heuristics and Behavioral Analysis
- Chapter 3: The Sandbox Era – New Battlegrounds and Advanced Evasion Strategies
- 3.1 Basic Sandbox Detection: Initial Fingerprinting of the Digital Cage
- 3.2 Advanced Sandbox Evasion Techniques: Outsmarting Modern Analyzers with Sophistication
- 3.2.1 Sophisticated Environment Fingerprinting and Human Interaction Analysis
- 3.2.2 Advanced Timing-Based Evasion and System Resource Exploitation
- 3.2.3 Logic Bombs, Environment Keying, and Debugger Detection in Sandbox Evasion
- Chapter 4: The Art of Concealment – Packers, Crypters, and the Rise of Metamorphic Stubs
- Chapter 5: Apex AV Evasion Techniques – Runtime Crypters, In-Memory Tactics & DLL Injection
- Chapter 6: DLL Injection for AV Evasion – A Deeper Dive into a Persistent Threat
- Conclusion: The Perpetual Evolution in the AV Evasion Arms Race
Introduction: The Unending Cybersecurity Arms Race – Understanding Antivirus Evasion Techniques
The intricate and ever-shifting domain of cybersecurity hosts an unceasing conflict. This ongoing battle pits digital frontier guardians against those who relentlessly seek to breach these defenses. Antivirus (AV) software serves as a principal defender in this critical arena. Indeed, AV software has proven indispensable for shielding computer systems from a myriad of malicious threats. However, these protective bulwarks have paradoxically fueled a parallel and sophisticated evolution: the development of AV evasion techniques. This article embarks on a comprehensive journey through the compelling history of these evasion tactics. We will trace their progression from rudimentary beginnings, such as basic code obfuscation, to highly advanced methodologies. These advanced methods prominently include Metamorphic Code Techniques, Advanced Sandbox Evasion Techniques, and various forms of DLL Injection for AV Evasion.
We will also explore sophisticated Runtime Crypter technology prevalent in today’s complex threat landscape. A thorough understanding of this perpetual cat-and-mouse game is not merely academic. Instead, it forms a critical necessity for cybersecurity professionals, researchers, and students alike.
These individuals strive to navigate the digital world’s complexities with greater security and heightened awareness. The insights gained from this exploration will illuminate the path towards more robust defensive strategies. These strategies are vital for countering diverse AV evasion techniques, including sophisticated sandbox bypass methods and advanced code transformation strategies. Understanding these advanced concepts, particularly the nuances of Metamorphic Code Techniques and Advanced Sandbox Evasion Techniques, is absolutely key to modern cybersecurity practice.
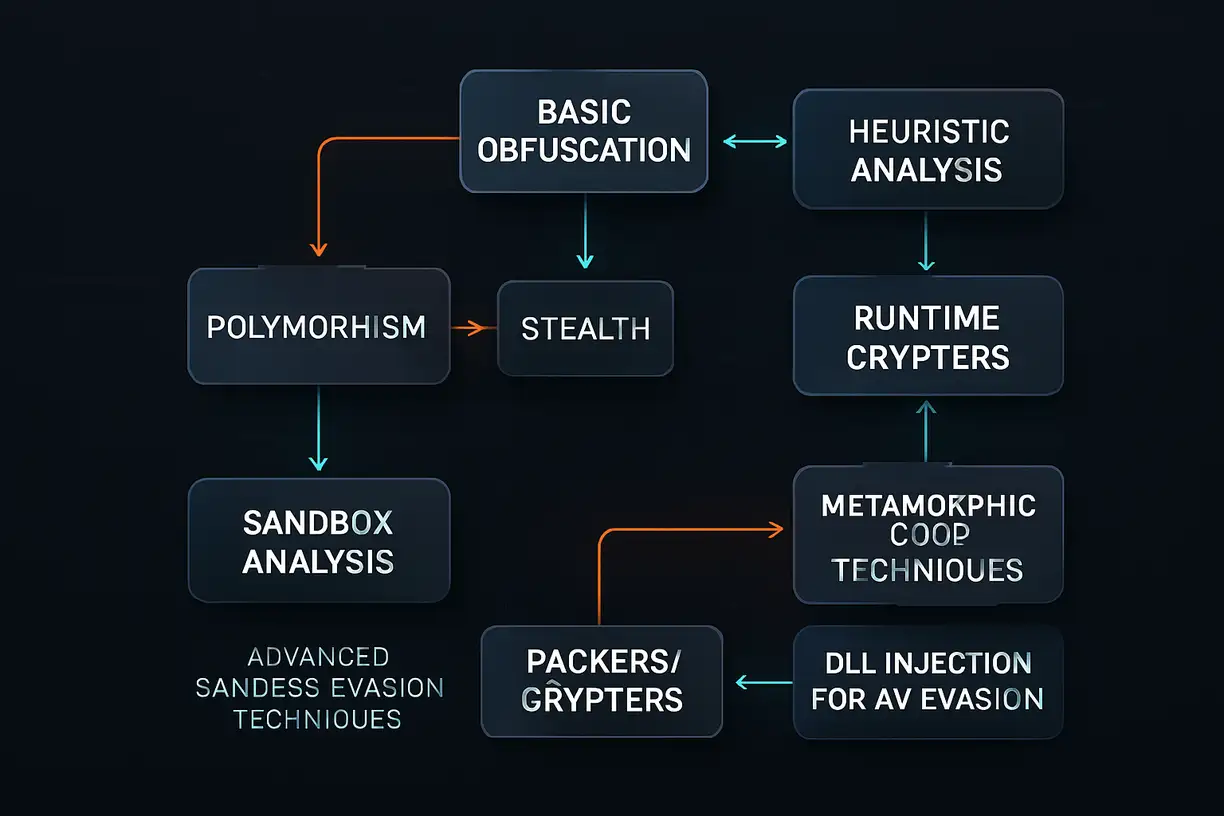
Metamorphic Code Techniques – Advanced Sandbox Evasion Techniques – DLL Injection for AV Evasion
Chapter 1: The Dawn of Evasion – Obfuscation, Stealth, and the Seeds of Code Transformation
The nascent era of personal computing witnessed the emergence of relatively unsophisticated viruses. Consequently, the first generation of antivirus programs primarily relied on a straightforward method: signature-based detection. This approach involved identifying known malware by its unique digital fingerprint or specific code sequence.
Malware authors, however, quickly adapted to these early defenses. They began employing basic obfuscation techniques. Their core aim was to alter their malicious code’s superficial appearance. This alteration allowed them to sidestep signature matches without fundamentally changing its harmful functionality.
This marked the first significant turn in the history of Antivirus evasion techniques. These early methods effectively paved the way for more complex strategies. This included the initial conceptual forms of Metamorphic Code Techniques, which would later become a significant challenge.
1.1 The Advent of Polymorphism: A Shifting Disguise in AV Evasion
Malware authors developed polymorphism as an early sophisticated AV evasion technique. This method allows malware to alter its own code or visible features during every infection or replication cycle. One can imagine a chameleon changing its colors to blend into different environments; polymorphic crypter malware achieved a similar effect in the digital realm.
Early polymorphic viruses used simple encryption algorithms. These algorithms employed variable keys for their main payload. They prepended this encrypted payload with a small, often variable, decryption routine. These viruses also employed code-shuffling routines within the decryptor itself.
Consequently, each infected file, while carrying the same malicious payload, would present a different signature to AV scanners. This variance occurred due to the varying decryptor and encryption key. This constant mutation significantly challenged static, signature-based detection systems. It forced AV vendors to develop more dynamic analysis methods. These methods included emulation or generic decryption routines, specifically to counter these evolving AV evasion techniques.
1.2 Embracing Stealth: Hiding in Plain Sight from Antivirus
Alongside polymorphism and the more advanced Metamorphic Code Techniques, stealth techniques emerged as another common evasion strategy. Malware authors designed certain early viruses to actively conceal their presence from the operating system and any resident antivirus software. Attackers often achieved this by intercepting system calls.. System calls are the communications between software and the operating system.
For instance, if an AV scanner requested to read a file that the virus had infected, the stealth virus might intercept this request. It would show an unmodified, clean version of the file to the scanner, hiding the infection.. Another common stealth tactic involved the virus temporarily removing itself from the system’s active memory when it detected an AV scan in progress. It would then silently re-infect the system once the scan concluded.
These early forays into stealth highlighted the malware authors’ growing understanding of system internals and AV operational patterns. These are key aspects of AV evasion techniques. Stealth remains a fundamental concept in sophisticated malware design. It often complements other advanced methods such as Advanced Sandbox Evasion Techniques and various forms of DLL Injection for AV Evasion.
1.3 Advanced Metamorphic Code Techniques: Deep Dive into Detection Challenges
Beyond polymorphism’s basic principles, Metamorphic Code Techniques involve malware completely rewriting its code with each new generation. This process makes each instance unique and significantly harder to detect. Advanced malware employs sophisticated strategies in this domain. These can include complex finite state machines guiding the mutation process.
This ensures the generated code remains functional while maximizing its diversity. Some metamorphic engines even incorporate machine learning elements. This allows them to adapt their transformation strategies based on the characteristics of the detection environment. AV vendors face immense challenges. Advanced code transformation renders traditional signature-based detection ineffective.
Even heuristic analysis struggles with the sheer variability of metamorphic code. Modern defenses increasingly rely on behavioral analysis, emulation, and machine learning models. These models identify underlying malicious intent, not specific code patterns. The arms race in this domain is particularly fierce. Researchers constantly explore new methods for both generating and detecting highly evasive metamorphic malware.
Understanding the nuances of advanced code transformation and self-mutating executable structures is critical for developing next-generation cybersecurity solutions. The sophistication of Metamorphic Code Techniques continues to push defensive boundaries, demanding innovative detection approaches.
1.3.1 The Intricacies of Metamorphic Engines and Their Evasion Power
Metamorphic engines are inherently complex. They must capably disassemble, analyze, transform, and then reassemble code. They perform all these actions while ensuring the malware’s core functionality remains intact. This process often involves sophisticated techniques borrowed from compiler theory, such as control flow graph manipulation.
The ultimate goal is to produce a syntactically different but semantically equivalent program each time it replicates. The effectiveness of Metamorphic Code Techniques hinges on the engine’s ability to generate highly diverse outputs. This diversity makes it computationally infeasible for AV scanners to maintain signatures for every possible variant. Some engines focus on conceptual instruction set randomization.
Others employ sophisticated code permutation malware strategies to alter structure. The continuous development of these engines underscores the dynamic nature of this AV evasion technique. These advanced engines are central to the challenge posed by Metamorphic Code Techniques, forcing defenders to look beyond simple pattern matching.
1.4 Entry Point Obscurity (EPO): A Classic Misdirection Tactic
Entry Point Obscurity (EPO) was a more targeted technique. It aimed at confusing AV scanners during their initial analysis. Most executable files have a defined starting point, or entry point, where the program’s execution begins. Signature-based AV scanners often focused their analysis on this entry point. They looked for known malicious patterns in this critical location. EPO viruses cleverly modified this entry point. They would typically insert a small piece of their own code at the original entry point.
This inserted code would then jump to the main body of the virus code, which was hidden elsewhere in the file, or even in a different file entirely. By obscuring the true starting location of the malicious payload, these viruses could often evade detection. Scanners not designed to trace these convoluted execution paths were particularly vulnerable to this tactic.
This technique underscored the need for more thorough and deep-scanning capabilities in AV solutions. EPO highlights the importance of analyzing the entire executable, a lesson that remains applicable to countering modern threats, including those that utilize DLL Injection for AV Evasion to hide their activities.
Chapter 2: Antivirus Countermeasures – The Rise of Heuristics and Behavioral Analysis
Malware, armed with early Antivirus evasion techniques like polymorphism, stealth, and nascent Metamorphic Code Techniques, grew in sophistication. As it did, the limitations of purely signature-based detection became increasingly apparent. The cybersecurity industry recognized the urgent need for more proactive and intelligent detection mechanisms. This recognition led to a significant evolution in AV technology.
The widespread adoption of heuristic analysis and behavioral detection marked this important shift. These new approaches moved the focus from simply identifying known threats to recognizing suspicious characteristics and actions, even in previously unseen malware. This was a pivotal moment in the ongoing arms race against AV evasion techniques.
AV solutions had to adapt quickly to these evolving threats to maintain their effectiveness. The development of these countermeasures was essential to combat the growing complexity of malware, including early forms of Advanced Sandbox Evasion Techniques.
2.1 Heuristic Analysis: Detecting the Suspicious Unknown Malware
Heuristic analysis represented a significant leap forward from reactive signature matching. Instead of looking for exact code sequences of known viruses, heuristic engines examine code for suspicious attributes or patterns. These patterns are commonly associated with malicious software. This could include the presence of unusual or rarely used system instructions. It might also involve attempts to directly manipulate hardware.
The inclusion of self-modifying code, a hallmark of polymorphic and Metamorphic Code Techniques, was another key indicator. Heuristics also looked for the use of known packing or encryption routines often employed by malware. If a program exhibited a sufficient number of these suspicious indicators, the AV software would flag it as potentially malicious. This flagging occurred even if its specific signature was not yet in the database.
This proactive approach was a direct response to evolving AV evasion techniques. This included the challenges posed by the advanced code transformation inherent in Metamorphic Code Techniques. Heuristics provided a crucial new defense layer against emerging threats, forcing malware to become even more subtle.
Chapter 3: The Sandbox Era – New Battlegrounds and Advanced Evasion Strategies
As AV vendors developed more sophisticated heuristic and behavioral analysis capabilities, malware authors were pushed to devise new AV evasion techniques. The sandbox became a significant hurdle for malware. A sandbox is a controlled, isolated environment. Security researchers and automated AV systems use it to safely execute and analyze suspicious files without risk to the underlying host system.
Sandboxes allowed for deep inspection of malware behavior. This made it harder for threats to go unnoticed. Consequently, a new generation of evasion tactics emerged. These tactics were specifically designed to detect and circumvent these analytical environments. We now refer to these as Advanced Sandbox Evasion Techniques.
The goal for malware authors was clear. If malware could ascertain it was operating within a sandbox, it could alter its behavior. It might choose to remain dormant. It could terminate itself. Or, it might present benign characteristics to avoid revealing its malicious capabilities. This marked a new frontier for AV evasion techniques. It led to a sophisticated arms race centered on anti-analysis techniques and sophisticated sandbox bypass strategies.
The development of Advanced Sandbox Evasion Techniques became a major focus for attackers seeking to remain undetected by modern security solutions. These techniques often work in conjunction with other methods like DLL Injection for AV Evasion.
3.1 Basic Sandbox Detection: Initial Fingerprinting of the Digital Cage
Malware authors initially focused on fingerprinting common sandbox environments. This involved checking for tell-tale signs indicating the program was running within a sandbox or virtual machine (VM) rather than on a genuine user system. Common methods included several types of checks. Artifact Checks involved searching for specific files (e.g., VBoxGuestAdditions.iso).
They also looked for registry keys (e.g., HKLMSOFTWAREOracleVirtualBox). Process names (e.g., vmtoolsd.exe, VBoxService.exe) or MAC address prefixes known to be associated with popular virtualization or sandboxing software (like VMware, VirtualBox, or Cuckoo Sandbox) were also targets. Hardware and Resource Anomalies involved checking for unusual hardware configurations often characteristic of default sandbox setups. Examples include a very small amount of RAM, a single CPU core, a small hard disk size, or generic display adapter names (e.g., “VirtualBox Graphics Adapter”).
Basic Timing Discrepancies exploited gross differences in how time is perceived or how certain operations are timed within virtualized versus physical environments. For example, some CPU instructions might execute at noticeably different speeds, or system uptime might be suspiciously short. Lack of User Activity involved monitoring for typical user interactions like mouse movements, keyboard inputs, browsing history, or recently opened documents.
Automated sandboxes often lack this organic user activity. Specific API Behavior involved querying Windows APIs that might return different values or behave slightly differently within a sandbox compared to a native system. These basic detection methods were the first step in the development of more Advanced Sandbox Evasion Techniques.
3.2 Advanced Sandbox Evasion Techniques: Outsmarting Modern Analyzers with Sophistication
As sandboxes became more adept at hiding common artifacts, malware evolved significantly. It began incorporating more Advanced Sandbox Evasion Techniques. These sophisticated sandbox bypass methods go far beyond simple checks. They aim to exploit more subtle characteristics or inherent limitations of analytical environments. Understanding these Advanced Sandbox Evasion Techniques is absolutely crucial for defenders to stay ahead in the cybersecurity landscape. These techniques often require intricate knowledge of system internals.
3.2.1 Sophisticated Environment Fingerprinting and Human Interaction Analysis
This advanced fingerprinting involves looking for more nuanced indicators of a sandbox. For instance, malware might check for the presence or absence of specific CPU features (e.g., via the CPUID instruction). These features are common in real hardware but might not be perfectly emulated in all virtual environments. It could also scrutinize driver details, loaded kernel modules, or the patch levels of system components, looking for inconsistencies typical of a controlled environment.
Some malware performs extensive checks for user-specific data. This includes the number of files in user directories, the depth of browser history, or specific application settings, which are often minimal or generic in sandboxes. While basic sandboxes might simulate simple mouse clicks or key presses, advanced malware looks for more complex patterns of human behavior. This can include analyzing the timing and velocity of mouse movements.
It also checks for non-linear mouse paths, or looks for evidence of scrolling, window resizing, or interaction with multiple applications. If user activity appears too programmatic or simplistic, the malware may identify the sandbox and alter its behavior. These methods are key components of modern Advanced Sandbox Evasion Techniques.
3.2.2 Advanced Timing-Based Evasion and System Resource Exploitation
Instead of just checking system uptime, more advanced malware can execute specific CPU instruction sequences (e.g., RDTSC). It then compares the execution times against expected values on native hardware. Virtualization overhead can introduce detectable latencies that sophisticated malware can identify. Similarly, API call completion times or the duration of specific computations can be measured and compared against a baseline to detect emulation or analysis environments. Some malware attempts to trigger behaviors or query artifacts unique to certain sandbox technologies.
This might involve attempting to communicate with known sandbox control channels or looking for specific named pipes used by analysis tools. Some even try to exploit known vulnerabilities within sandbox software itself to escape confinement or disable monitoring capabilities. These anti-analysis techniques are hallmarks of Advanced Sandbox Evasion Techniques, demonstrating a deep understanding of how sandboxes operate.
3.2.3 Logic Bombs, Environment Keying, and Debugger Detection in Sandbox Evasion
Advanced Sandbox Evasion Techniques also frequently include the use of logic bombs and environment keying. Malware might employ environment keying, activating its malicious payload only if specific, non-standard system configurations are detected. These are configurations unlikely to be present in a generic sandbox environment. This could involve checking for unique files, specific registry keys, or particular network shares that indicate a real user system.
Another sophisticated approach exploits subtle timing differences in CPU instruction execution or API call responses, which can betray virtualization. Furthermore, many types of malware actively detect the presence of common debugging tools. They will remain dormant or terminate their execution if such tools are identified during their initial checks. These anti-analysis techniques and sophisticated sandbox bypass strategies and bypass false positive AV detections require equally advanced detection mechanisms from the defense side.
This includes methods like dynamic taint analysis or symbolic execution to trace potential execution paths. The continuous evolution of Advanced Sandbox Evasion Techniques necessitates ongoing research and development of robust countermeasures by security vendors.
Chapter 4: The Art of Concealment – Packers, Crypters, and the Rise of Metamorphic Stubs
As AV detection capabilities, including sandboxing and advanced heuristics, grew more robust, malware authors increasingly turned to sophisticated obfuscation methods. These primarily involved the use of advanced packers and crypters. While packing, which involves compressing executables, initially served legitimate purposes like reducing file size, malware creators quickly co-opted it as an effective evasion layer.
Crypters took this concept further. They focused on encrypting the malware payload to prevent static analysis and signature-based detection. This phase in malware evolution marked a significant escalation in Malware Encryption complexity. It also saw the more profound application of Metamorphic Code Techniques within the stubs and loaders of packed or encrypted malware. These are all integral parts of advanced AV evasion techniques, designed to make malware analysis more difficult.
4.1 Packers: Compressing and Obscuring Malicious Payloads Effectively – AV evasion techniques
Packers are utilities that compress and/or encrypt an executable file. They embed the original code within a new executable shell or stub. When someone runs the packed executable, this stub code first unpacks or decrypts the original malicious payload into memory. Then, it transfers execution control to this payload.
The benefits for malware authors were manifold. Signature Evasion occurred because packing significantly alters the file’s on-disk signature, making it different from known malware signatures. Anti-Static Analysis meant that static analysis tools found it hard to examine the packed code directly. The malicious logic remained hidden until runtime. Popular packers like UPX, initially developed for legitimate software compression, were frequently abused by malware authors.
Malware authors also developed custom packers specifically designed for evasion. These custom packers often incorporated anti-debugging and anti-VM tricks within the unpacking stub itself. These are AV evasion techniques focused on the loader. Some of these loaders even began to use early forms of Metamorphic Code Techniques in their stubs to further complicate detection.
4.2 Crypters: Advanced Encryption and the Emergence of Metamorphic Stubs
Crypters are specialized tools that malware authors design to encrypt a payload and bundle it with a decryption stub. The primary goal of using a crypter is to make the malware Fully Undetectable (FUD) by AV software, at least temporarily. Unlike generic packers, crypters often use sophisticated and frequently updated encryption algorithms (such as AES, RC4, or custom ciphers). Their stub code is meticulously designed to evade detection by AV heuristics and behavioral analysis.
The process typically involves Payload Encryption and Stub Generation. The stub contains the decryption logic and the encrypted payload. It is designed to be as inconspicuous as possible. Here, crypters significantly advance evasion capabilities: Polymorphic and Metamorphic Stubs. Advanced crypters generate unique or heavily modified stubs for each encrypted payload. The most sophisticated among them employ Metamorphic Code Techniques for their stubs. This means the stub’s code structure is fundamentally altered with each generation.
This alteration uses techniques like instruction substitution, code permutation, and garbage code insertion, as detailed earlier in the context of Metamorphic Code Techniques. This advanced code transformation makes signature-based detection of the stub exceptionally challenging. The stub might also incorporate anti-debugging measures, anti-VM checks, and various Advanced Sandbox Evasion Techniques. These checks are often performed before the main payload is decrypted. This layering of defenses is a hallmark of modern crypters.
The effectiveness of a crypter is often fleeting as AV vendors adapt and update their detection signatures and heuristics. In response, crypter developers release new versions with more sophisticated instruction set randomization or code permutation strategies to stay ahead, constantly refining their AV evasion techniques. The use of Metamorphic Code Techniques in these stubs is a key factor in their ongoing success against detection.
Chapter 5: Apex AV Evasion Techniques – Runtime Crypters, In-Memory Tactics & DLL Injection
The evolution from basic crypters to dynamic, elusive malware concealment methods led to the development of Advanced Runtime Crypter Technology. This represents a paradigm shift in Malware Encryption and evasion. It focuses on minimizing the malware’s memory footprint and execution visibility. Traditional crypters, even those with metamorphic stubs, typically decrypt their entire payload into memory at once. This can be a strong indicator for behavioral analysis or memory scanning by security software.
Advanced Runtime Crypters, sometimes known as staged crypters or multi-stage packers, use far more insidious techniques. These are central to modern Antivirus evasion techniques. They often include sophisticated methods for process injection via DLL or other means, such as various forms of DLL Injection for AV Evasion, to hide their presence and activity.
5.1 Decryption on Demand and Staged Execution as AV evasion techniques
A key characteristic of an Advanced Runtime Crypter is its ability to decrypt and execute the payload in stages or on demand, often directly in memory. Instead of exposing the entire decrypted malware simultaneously, it might employ Decrypt Small Chunks (often referred to as Function-by-Function Decryption).
It only decrypts small portions of its code just before they are needed for execution. Once executed, the memory containing the decrypted code might be wiped clean or re-encrypted, significantly reducing the detection window for memory scanners. It might also use Execute-Only Memory, leveraging memory protection flags (e.g., DEP – Data Execution Prevention, though malware aims to bypass it) to make analysis harder by preventing reading or modification of executed code. Multi-Stage Loaders are common: an initial, small stub decrypts a second-stage loader.
This second stage might perform more extensive environment checks (incorporating more Advanced Sandbox Evasion Techniques) before fetching or decrypting the main malicious payload. Each stage in this process can use different encryption algorithms and keys. Some runtime crypters use Direct In-Memory Mapping/Loading. This avoids traditional PE (Portable Executable) loading mechanisms. Instead, it manually maps sections of the malware into memory and resolves imports on the fly.
This approach bypasses many OS-level hooks and monitoring points that rely on standard PE loading events. These methods are critical for modern malware seeking to evade detection. They often combine these techniques with DLL Injection for AV Evasion to further obscure their operations.
5.2 Process Injection: Hiding Malicious Code Within Legitimate Processes
To further evade detection and gain persistence or elevated privileges, advanced runtime crypters frequently employ process injection techniques. This involves housing malicious code within the memory space of legitimate, trusted processes. This makes the malware activity appear to originate from a benign source, complicating detection by security software. DLL Injection for AV Evasion is a prominent and versatile method used in this context.
Classic DLL Injection involves forcing a legitimate process to load a malicious DLL. This is often achieved using API calls like CreateRemoteThread in conjunction with LoadLibrary. The malicious DLL, once loaded into the target process’s address space, executes its payload, benefiting from the host process’s trust and privileges.
The DLL itself might be packed or use Metamorphic Code Techniques to avoid detection on disk or during loading. Process Hollowing (also known as RunPE) is a more aggressive technique. Here, a legitimate process is created in a suspended state. Its primary executable image is then unmapped from memory and replaced with the malware’s code.
The process is then resumed, now running the malicious code under the guise of the original legitimate application. Thread Execution Hijacking involves modifying the execution context of an existing thread within a target process to redirect its execution flow to malicious shellcode injected into that process. Asynchronous Procedure Call (APC) Injection queues an APC to a target thread.
This APC will execute malicious code when the thread enters an alertable state. This is often a stealthier way to achieve code execution compared to creating new remote threads, making it a subtle form of DLL Injection for AV Evasion. These techniques, especially when combined with staged decryption and Metamorphic Code Techniques for the injected components, make detection very difficult.
The malware effectively dissolves into the normal operational noise of the system. The sophistication of DLL Injection for AV Evasion continues to challenge defenders significantly, requiring advanced behavioral monitoring and memory analysis.
5.3 Defeating Forensics: Advanced AV Evasion Techniques Against Memory Analysis
Runtime crypters also incorporate features specifically designed to counter memory forensics and advanced behavioral analysis tools. Anti-Memory Dumping techniques attempt to detect or prevent security tools from acquiring a clean image of the decrypted malicious code from memory.
This could involve encrypting critical data structures in memory when not in immediate use, or hooking memory access APIs to provide fake data to analysis tools. API Call Obfuscation/Redirection is another common tactic. Instead of calling sensitive Windows APIs directly (which are often monitored by EDR solutions), malware might use indirect calls, jump through a series of trampolines, or use syscalls directly to bypass user-mode hooks. Some malware resolves API addresses dynamically at runtime to make static analysis of its import table less revealing.
Clearing Traces involves actively wiping sensitive information from memory after use. This includes cryptographic keys, decrypted code sections, or intermediate data. Understanding Advanced Runtime Crypter Technology is paramount for modern cybersecurity. This includes their reliance on advanced code transformation, sophisticated sandbox bypass strategies, and various methods of process injection via DLL (a key form of DLL Injection for AV Evasion).
This knowledge is crucial for developing effective, next-generation defenses. These defenses need to incorporate nuanced behavioral biometrics, in-depth memory analysis capabilities, and potentially AI-driven anomaly detection to identify these stealthy threats.
Chapter 6: DLL Injection for AV Evasion – A Deeper Dive into a Persistent Threat
DLL Injection for AV Evasion warrants a detailed examination as it remains a cornerstone technique for malware. It allows malware to achieve stealth, persistence, and sometimes privilege escalation by running malicious code under the guise of a legitimate process. This method of process injection via DLL is favored by attackers because it can bypass basic process-based allowlisting and Host Intrusion Detection Systems (HIDS) that primarily monitor for the creation of new suspicious processes.
It also allows the malicious code to inherit the privileges and trust level of the target process. The versatility and effectiveness of DLL Injection for AV Evasion make it a persistent and dangerous threat in the ever-evolving cybersecurity landscape. Understanding its various forms is crucial for defense.
6.1 Core Mechanisms of DLL Injection: A Step-by-Step Explanation
The fundamental principle behind most forms of DLL injection involves several key steps. First, Target Process Identification: the malware identifies a suitable target process. Common targets include system processes like explorer.exe or svchost.exe, or other widely used applications. Second, Memory Allocation in Target Process: the malware allocates a region of memory within the target process’s virtual address space.
This memory will be used to store the path to the malicious DLL or, in some cases, the malicious code itself. Third, Writing to Target Process Memory: the path to the malicious DLL or the shellcode is written into this allocated memory space within the target process.
Finally, Forcing DLL Load/Code Execution: the malware triggers the target process to load the specified DLL or execute the injected code. These steps are fundamental to most DLL Injection for AV Evasion strategies. Mastery of these steps and their variations is common among malware authors seeking to evade detection.
6.2 Common DLL Injection Techniques and Their Evasion Tactics
Several distinct techniques are commonly used for DLL Injection for AV Evasion, each with its own nuances for bypassing security measures. The CreateRemoteThread with LoadLibrary method is a classic approach. In this technique, malware calls VirtualAllocEx to allocate memory in the target, WriteProcessMemory to write the DLL path, and then CreateRemoteThread to start a new thread in the target process.
This new thread’s starting routine is set to the address of the LoadLibrary function, with the argument being the path to the malicious DLL. AV solutions often monitor these API calls. Evasion Aspect: if the source process initiating the injection is trusted, or if the DLL path is obfuscated or loaded from an unusual location, it might slip past basic detection. Asynchronous Procedure Call (APC) Injection is generally considered stealthier. It queues an APC to an existing thread within the target process. This APC will execute malicious code (which could load a DLL) when the thread enters an alertable state.
This method of process injection via DLL (indirectly, by first injecting code to load it) is harder to detect based on new thread creation events. Evasion Aspect: it avoids the direct CreateRemoteThread signatures that many security tools look for. Reflective DLL Injection is a more advanced and fileless technique. Here, the malware maps its own DLL into the target process’s memory manually. It parses the PE headers, resolves necessary imports, and handles relocations itself, all without the DLL ever touching the disk of the target system. Evasion Aspect: this is highly effective against file-based AV scanning and basic LoadLibrary monitoring. Detection requires sophisticated memory analysis and anomaly detection.
Thread Execution Hijacking (sometimes referred to as Suspend, Inject, Resume – SIR) targets an existing thread in a process, suspends it, modifies its instruction pointer to point to injected shellcode (which could then load a DLL), and then resumes the thread. Evasion Aspect: this bypasses detection mechanisms focused on the creation of new threads. SetWindowsHookEx Injection uses the legitimate Windows API SetWindowsHookEx to install a global hook procedure.
This hook procedure resides in a malicious DLL, which is then loaded into the address space of every GUI process on the desktop when specific events occur (like keyboard or mouse input). Evasion Aspect: it leverages a legitimate Windows mechanism, making it harder to distinguish from benign activity. These varied approaches to DLL Injection for AV Evasion demonstrate attacker ingenuity and the continuous need for robust and adaptive defenses.
6.3 Defending Against DLL Injection: Countering These AV Evasion Techniques
Defending against the diverse methods of DLL Injection for AV Evasion requires a comprehensive, multi-layered security approach. Monitoring API Calls is crucial. Modern security software, particularly Endpoint Detection and Response (EDR) solutions, closely monitors suspicious calls to APIs frequently used in injection techniques.
These include CreateRemoteThread, VirtualAllocEx, WriteProcessMemory, QueueUserAPC, NtMapViewOfSection, and SetWindowsHookEx. Security tools look for anomalous patterns or combinations of these calls. Memory Scanning and Analysis is also critically important. Advanced AV/EDR solutions perform regular and on-demand memory scans of running processes to detect reflectively loaded DLLs, injected shellcode, or other in-memory anomalies that might indicate a successful injection.
Behavioral Analysis plays a key role by profiling the normal behavior of processes and flagging deviations. For example, if a typically non-network-facing process suddenly starts making network connections after a suspected injection, it would be flagged. Attack Surface Reduction, by implementing principles like least privilege, limits the impact of a successful injection by ensuring that compromised processes do not have unnecessary permissions.
DLL Allowlisting/Blocklisting, while challenging to implement and maintain comprehensively, can help control which DLLs specific critical processes are permitted to load. The continuous evolution of DLL Injection for AV Evasion techniques, including variations that leverage obscure APIs or combine injection with other anti-analysis techniques like those used in Advanced Sandbox Evasion Techniques, ensures that this remains a critical focus area for cybersecurity research and defense. Robust defenses, capable of detecting both known and unknown injection patterns, are essential against sophisticated DLL Injection for AV Evasion and its many variants.
Conclusion: The Perpetual Evolution in the AV Evasion Arms Race
The journey through the history of Antivirus evasion techniques, from elementary obfuscation and polymorphism to the sophisticated realms of Metamorphic Code Techniques, Advanced Sandbox Evasion Techniques, intricate DLL Injection for AV Evasion, and the dynamic stealth of runtime crypters, paints a clear picture of a relentless technological arms race. Each defensive innovation by AV vendors has been met with increasingly ingenious and complex evasion strategies from malware authors. This constant co-evolution underscores a fundamental truth in cybersecurity: there is no permanent silver bullet.
For students, researchers, and industry professionals, understanding this evolutionary trajectory is paramount. It is not merely a historical account but a vital lesson in the adaptive nature of cyber threats. The shift towards advanced code transformation, sophisticated sandbox bypass strategies, and stealthy process injection via DLL and other in-memory execution methods highlights the limitations of purely signature-based or simplistic heuristic approaches. Modern defenses must be agile, multi-layered, and capable of deep behavioral analysis, memory forensics, and anomaly detection. For more ways we recommend join our Telegram Channel.
The pursuit of more robust security measures necessitates continuous research into these advanced evasion tactics. By dissecting how Metamorphic Code Techniques can create near-infinite unique malware instances, how Advanced Sandbox Evasion Techniques can trick analytical environments, and how DLL Injection for AV Evasion can allow malware to masquerade as legitimate processes, the cybersecurity community can better anticipate and neutralize future threats.
The challenge lies not only in detecting known evasion patterns but also in building resilient systems that can identify and respond to novel forms of attack. As we look to the future, the integration of machine learning for anomaly detection, advancements in hardware-assisted security, and a deeper understanding of adversarial AI will likely play crucial roles in tipping the scales in this ongoing battle to protect our digital ecosystems. Data Encoder will help you for secure software from false positive detections and any give the best secure ways.


Leave A Comment