- DNS Tunneling: Data Exfiltration and C2 Over Port 53
- Fast Flux DNS: The Ephemeral C2 Infrastructure
- Domain Generation Algorithms (DGAs): Defeating Blocklists
- SSL/TLS and CDN Abuse: The "Legitimate" Facade
- Emerging Evasion Tactics in 2025: Beyond Traditional Methods
- FAQ: Technical Questions Answered for Defenders
- Final Recommendations for Defenders
In 2025, Hackers erase traces They employ DNS Tunneling, Cloudflare’s proxified DNS, and SSL/TLS with Fast Flux DNS. Additionally, they utilize Domain Generation Algorithms (DGAs), IP spoofing, port hopping, and polymorphic crypter techniques. the average enterprise deploys a layered defense stack: next-generation firewalls (NGFW), endpoint detection and response (EDR), secure web gateways (SWG), DNS filtering, and cloud access security brokers (CASBs). These systems continuously monitor for anomalies in:
- Source/destination IP addresses
- Domain reputation and registration age
- TLS certificate fingerprints
- DNS query frequency, entropy, and record types
- Behavioral patterns (e.g., process injection, unusual outbound connections)
To survive in such an environment, advanced persistent threats (APTs) and financially motivated cybercrime groups must erase or obfuscate every traceable artifact. They don’t just want initial access—they want persistent, undetectable command-and-control (C2) channels that blend into normal traffic.
This is why modern malware families—such as LummaStealer, Rhadamanthys, SystemBC, and IcedID—routinely integrate DNS tunneling, Fast Flux DNS, Domain Generation Algorithms (DGAs), SSL/TLS encryption, and cloud service abuse into their C2 infrastructure.
Understanding these techniques isn’t optional for defenders. It’s essential.
Disclaimer: This article is written exclusively for cybersecurity defenders, incident responders, SOC analysts, threat hunters, and network administrators. All techniques described are observed in real-world attacks and documented by CISA, MITRE, and industry threat intelligence. No offensive tools, malware samples, or exploit code are provided or endorsed.
DNS Tunneling: Data Exfiltration and C2 Over Port 53
DNS (Domain Name System) was never designed to carry application-layer data. Yet its ubiquitous allow-list status—almost all networks permit outbound DNS on UDP/TCP port 53—makes it ideal for covert channels.
How DNS Tunneling Works at the Protocol Level
In a DNS tunneling attack, malware on a compromised host encodes stolen data or C2 commands into DNS queries. These queries are sent to a domain controlled by the attacker. The attacker’s DNS server decodes the query, processes the command, and encodes the response into DNS answer records (typically TXT, NULL, or CNAME).
For example:
- Malware wants to exfiltrate a file named passwords.txt.
- It splits the file into 32-byte chunks and Base32-encodes each.
- It sends DNS queries like: aGVsbG8ud29ybGQucGFzc3dvcmRzLmV4YW1wbGUuY29t → resolves to attacker’s DNS
- The attacker’s server responds with: TXT “AQIDBAUGBwgJCgsMDQ4PEBESExQVFhc=” which the malware decodes as the next instruction.
This entire exchange bypasses HTTP/HTTPS proxies, firewalls, and DLP systems because it appears as standard DNS traffic.
Common DNS Tunneling Tools Observed in the Wild
While older tools like dnscat2 and iodine are well-known, modern malware uses custom, obfuscated implementations:
- SystemBC: A proxy-based malware that uses DNS tunneling as a fallback C2 channel when HTTP fails.
- Cobalt Strike: Supports DNS beacons with configurable subdomain lengths and encoding schemes.
- NjRAT variants: Use TXT records to send screenshots and keystroke
Detection: Behavioral and Statistical Indicators
Defenders should monitor for the following high-fidelity signals:
- Abnormally long subdomains: Legitimate domains rarely exceed 30 characters in subdomain length. Malicious tunnels often use 60+.
- High entropy in subdomain names: Random-looking strings (e.g., x9k2m4n8q1.data-exfil[.]com) have Shannon entropy > 4.2.
- Excessive use of TXT or NULL records: Normal DNS uses A/AAAA/CNAME. TXT is rare in client queries.
- Low query-to-response ratio: Tunneling clients send many queries but receive few answers.
- Repetitive query patterns with slight variations: Indicates data chunking.
Defensive Architecture Recommendations
- Deploy DNS logging at the recursive resolver level (e.g., BIND, Unbound, or enterprise DNS like Cisco Umbrella).
- Integrate Zeek (Bro) with custom scripts to calculate entropy and flag anomalies.
- Use ML-based classifiers trained on DGA and tunneling features and use data Encoder and secure your data.
- Block public DNS resolvers (e.g., 8.8.8.8) via firewall to force internal DNS use—enabling full visibility.

Fast Flux DNS: The Ephemeral C2 Infrastructure
Fast Flux is not a single technique—it’s a spectrum of evasion strategies designed to dynamically rotate infrastructure.
Single Flux DNS
- The domain’s A records (IPv4 addresses) change rapidly—often every 1–5 minutes.
- Achieved by setting low TTL (Time-to-Live) values (e.g., 30 seconds) and using a botnet to register new IPs.
- All IPs point to compromised hosts (zombies) that forward traffic to the real C2.
Example: malware[.]com → resolves to 185.12.34.5, 45.67.89.10, 103.45.67.88 within 10 minutes.
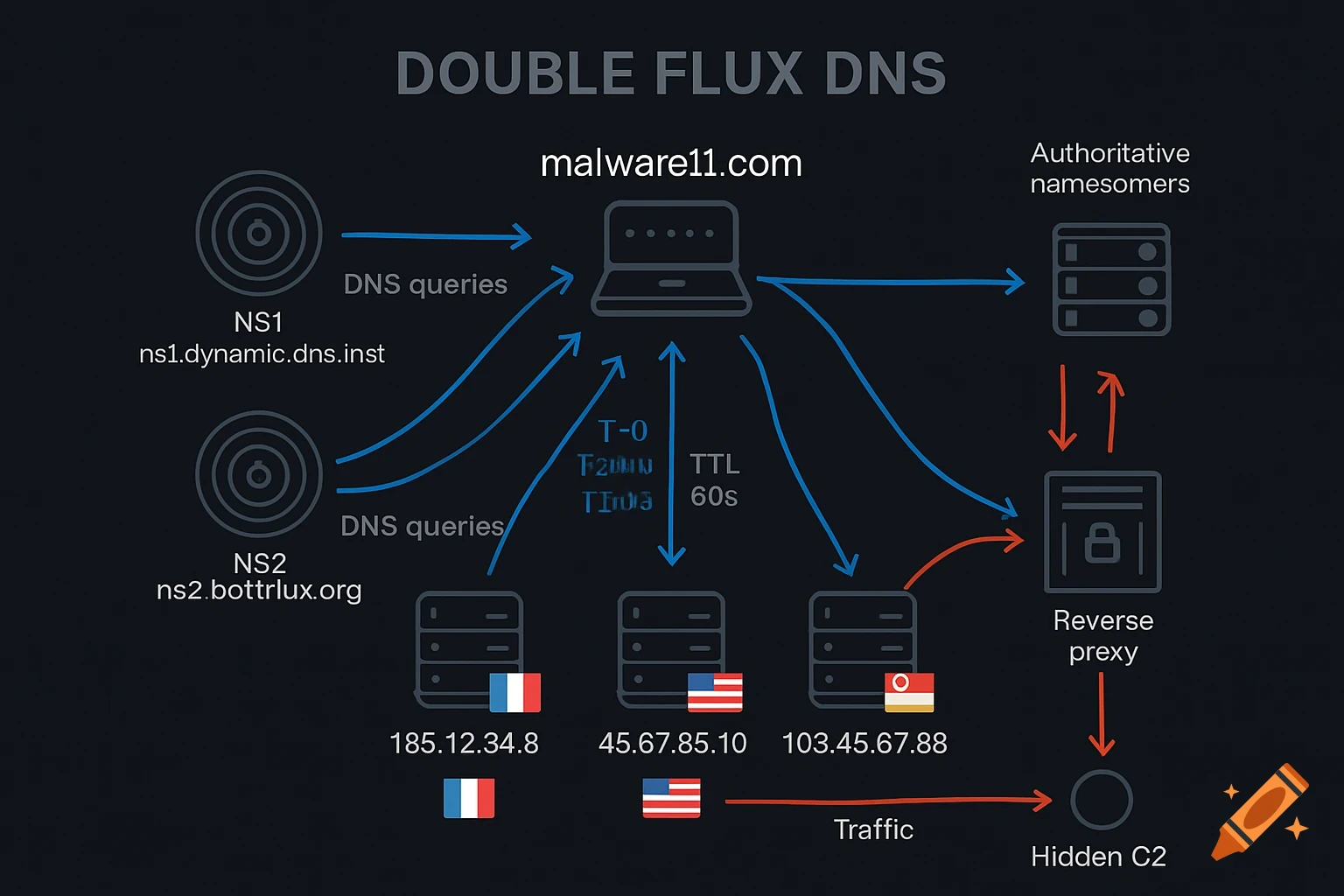
Double Flux DNS
- Both A records and NS (nameserver) records rotate.
- The attacker registers multiple dynamic DNS providers as authoritative nameservers.
- Each nameserver resolves the domain to a different set of IPs.
This makes takedowns nearly impossible—blocking one IP or nameserver has no effect.
Real-World Usage: From Conficker to LummaStealer
- Conficker (2008): Pioneered DGA + Fast Flux.
- Pushdo/Cutwail (2010s): Used double flux with 10,000+ IPs.
- LummaStealer (2024): Hosts C2 on Cloudflare-proxied domains with Fast Flux + DGA hybrid.
Detection Techniques of Fast Flux DNS
- Passive DNS Monitoring: Use services like SecurityTrails, RiskIQ, or Cisco Talos Intelligence to track IP churn.
- TTL Analysis: Domains with consistent TTL < 180 seconds are suspicious.
- Geolocation Dispersion: If a single domain resolves to IPs in Brazil, Russia, Singapore, and Germany simultaneously—red flag.
- Autonomous System (AS) Diversity: Fast Flux domains often resolve to IPs across dozens of ASNs.
Mitigation Strategy
- Sinkhole Fast Flux domains by preemptively registering DGA outputs (used by law enforcement).
- Deploy DNS firewall rules to block domains with high IP volatility.
- Integrate threat intel feeds that track active Fast Flux operators.
Domain Generation Algorithms (DGAs): Defeating Blocklists
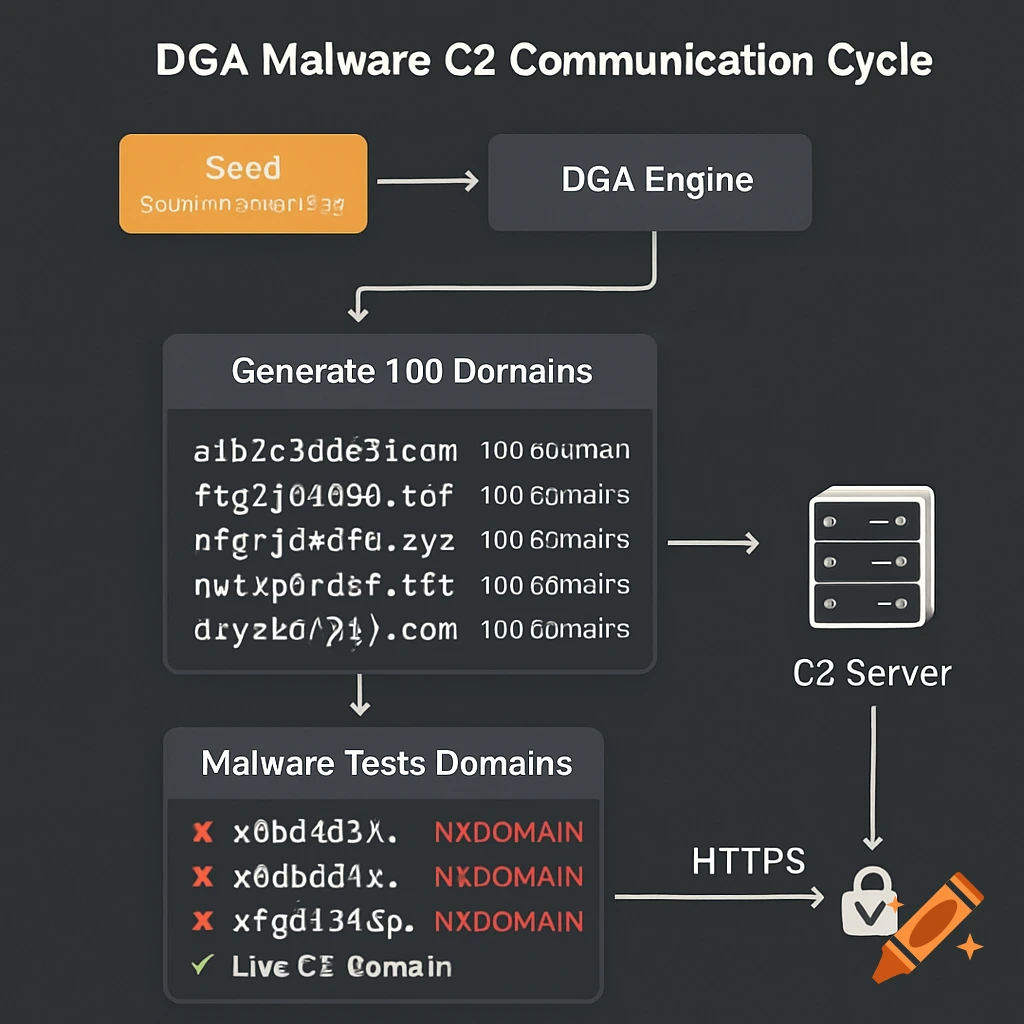
A DGA is a deterministic function that generates a large set of domain names daily. Both the malware and the attacker use the same seed (e.g., current date), so they can independently compute the same list.
Example algorithm (simplified Python-like pseudocode):
python
import datetime
seed = datetime.date.today().strftime(“%Y%m%d”)
domains = []for i in range(100):
domain = md5(seed + str(i)).hexdigest()[:10] + “.com”
domains.append(domain)
On January 1, 2025, this might produce:
- a1b2c3d4e5[.]com
- f6g7h8i9j0[.]com
- …
The attacker only registers 1–3 domains. The malware cycles through the list until it finds a live one.
Why DGAs Defeat Traditional Security
- Blocklists can’t pre-register 10,000 domains/day.
- Heuristic AVs can’t flag domain strings as malicious—they look like random noise.
- Sandboxing fails if the DGA seed is time-based and the sandbox runs on a different day.
Advanced DGA Variants in 2025
- Context-Aware DGAs: Seed includes local system info (e.g., username, MAC address)—making domains unique per victim.
- Dictionary-Based DGAs: Use real words (e.g., apple-orange-cloud[.]net) to bypass lexical detectors.
- TLD-Rotating DGAs: Generate .com, .net, .xyz, .top to avoid TLD-based filtering.
Detection: Machine Learning and Network Telemetry
- Lexical Analysis: Train models on features like:
- Vowel-to-consonant ratio
- n-gram frequency
- Domain length
- Network Behavior: Look for high NXDOMAIN (non-existent domain) error rates from a single host.
- Threat Intelligence: Use feeds like DGArchive or Cisco’s DGA classifier.
Defensive Tools For DGAs
- Cisco Umbrella: Blocks DGA domains in real-time.
- Palo Alto WildFire: Identifies DGA behavior in sandbox.
- Open-source: pyDGA, dga-detection (GitHub)
SSL/TLS and CDN Abuse: The "Legitimate" Facade
Modern attackers never host C2 on raw IP addresses. Instead, they:
- Register a domain (e.g., update-service[.]net)
- Point it to Cloudflare and enable the orange-cloud proxy
- Obtain a free Let's Encrypt TLS certificate
- Host C2 on a compromised VPS or serverless function
Result: All traffic appears as HTTPS to a trusted CDN, with valid TLS and no direct IP exposure.
Cloudflare's proxy hides the origin server IP, making takedowns require legal requests—not just IP blocking.
SSL/TLS Fingerprinting for Detection
Not all TLS is equal. Tools like JA3 (for clients) and JA3S (for servers) capture:
- TLS version
- Cipher suites
- Extensions order
Malware like Cobalt Strike or Sliver has distinct JA3 hashes. Defenders can:
- Feed JA3 hashes into SIEM (e.g., Splunk, Elastic)
- Alert on known malicious fingerprints
- Block unknown TLS clients from critical assets
Defensive Recommendations
- Inspect TLS metadata without decryption (via Zeek, Suricata, or commercial NGFW)
- Block domains with newly issued Let's Encrypt certs unless allowlisted
- Monitor for TLS sessions with low data volume (typical of beacons)
Emerging Evasion Tactics in 2025: Beyond Traditional Methods
Protocol Tunneling Over HTTP/2 and WebSockets:
Modern malware now abuses application-layer protocols to mimic legitimate SaaS traffic.
WebSocket Tunneling
- WebSockets (wss://) allow full-duplex communication over a single HTTPS connection.
- Malware establishes a WebSocket to api.google-analytics[.]com (spoofed) and sends C2 commands as JSON frames.
- Since WebSockets are used by Slack, Teams, and Zoom, they blend seamlessly.
Example (malicious WebSocket frame):
HTTP/2 Multiplexing Abuse
- HTTP/2 allows multiple streams over one TCP connection.
- Malware sends C2 as stream ID 5, while fake "browser traffic" uses stream ID 1.
- Firewalls that don't parse HTTP/2 see only one encrypted flow.
Detection: Use deep packet inspection (DPI) that supports HTTP/2 and WebSocket decoding. Tools: Zeek with HTTP/2 plugin, Arkime.
DNS-over-HTTPS (DoH) and DNS-over-TLS (DoT) Abuse
Enterprises increasingly allow DoH (e.g., to cloudflare-dns.com) for privacy. But attackers use it to:
- Hide DNS tunneling inside encrypted HTTPS
- Bypass DNS filtering appliances
Since DoH traffic is indistinguishable from regular HTTPS, traditional DNS monitors are blind.
Defense:
- Block public DoH resolvers via firewall (allow only internal DoH)
- Deploy TLS inspection to decrypt and analyze DoH traffic
- Use Encrypted DNS analytics in platforms like Cisco Secure Firewall
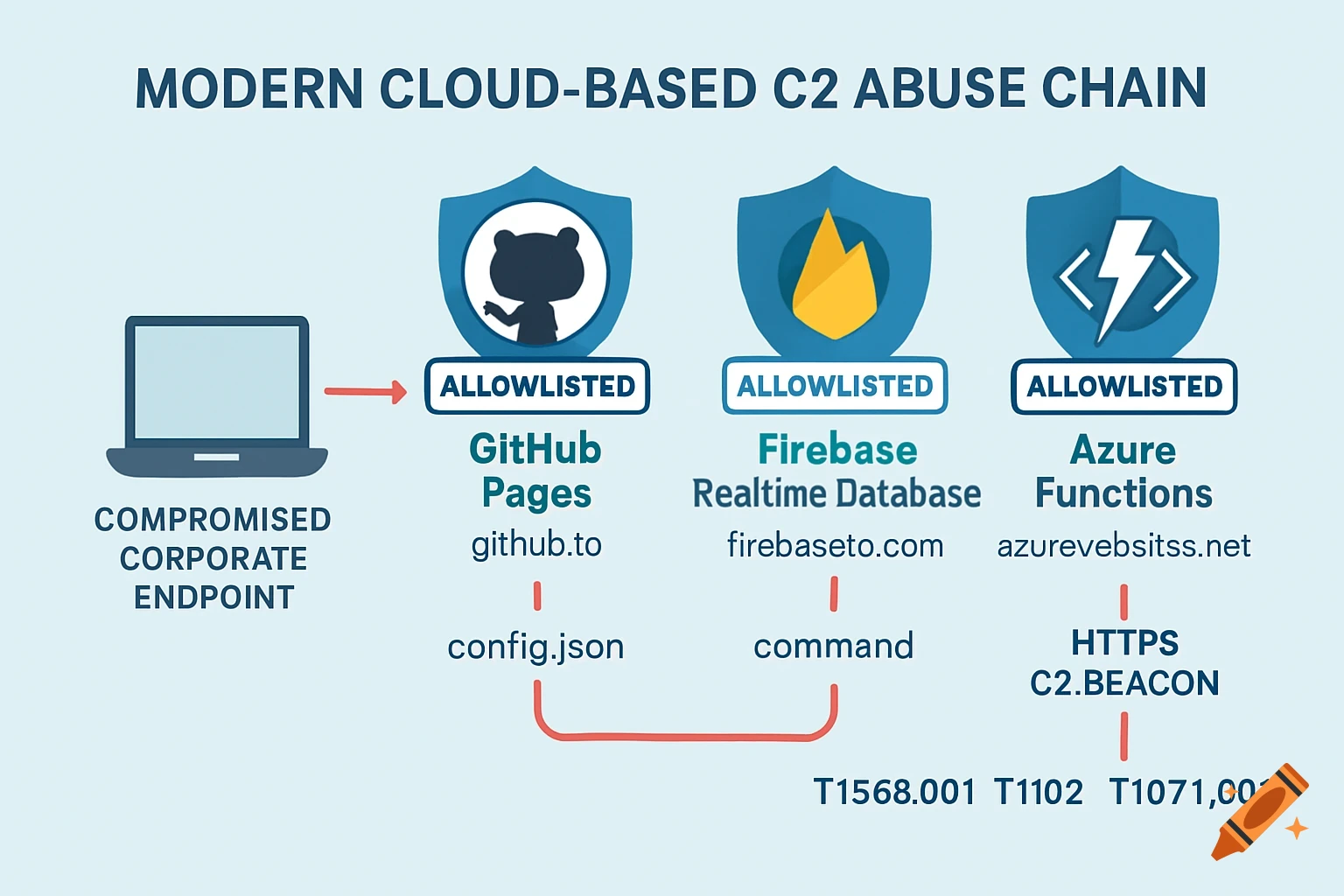
Cloud Service Abuse: GitHub, Firebase, Azure Functions
Attackers now host C2 payloads on trusted SaaS platforms:
- GitHub Pages: Host static C2 config at attacker.github.io/config.json. Read more about role of GitHub in spreading malware.
- Firebase Realtime Database: Store commands in a public DB (e.g., https://malware-default-rtdb.firebaseio.com/)
- Azure Functions: Deploy serverless C2 that scales automatically
These domains (github.io, firebaseio.com, azurewebsites.net) are allowlisted by most WAFs and proxies.
Detection Strategy For DNS-over-HTTPS:
- Monitor for unusual outbound calls to SaaS APIs from non-browser processes
- Use Cloud Access Security Brokers (CASBs) like Netskope or McAfee MVISION
- Deploy UEBA (User and Entity Behavior Analytics) to flag anomalous SaaS usage
FAQ: Technical Questions Answered for Defenders
What’s the difference between DNS tunneling and DGA?
DNS tunneling transports data over DNS queries. DGA generates domain names for C2 communication. They are often used together: DGA picks the domain, DNS tunneling sends the data.
Can EDR solutions like CrowdStrike detect Fast Flux?
Not directly—but if EDR is integrated with network telemetry, it can flag rapid domain-to-IP changes and unusual DNS behavior from a host.
Is it possible to block all DGA domains?
No—but you can sinkhole high-probability DGAs using predictive models. Alternatively, block all newly registered domains (NRDs) for high-risk users.
Does enabling DNSSEC prevent DNS tunneling?
No. DNSSEC ensures integrity and authenticity of DNS records—it doesn’t restrict data volume or record types. Tunneling still works.
How do I simulate these attacks for training?
Use CALDERA, Atomic Red Team, or MITRE Engenuity scenarios. Never use real malware or Telegram channels.
Are there legal risks to researching these techniques?
Yes. Always operate in isolated labs, comply with local laws, and avoid interacting with live C2 infrastructure.
Final Recommendations for Defenders
- Assume breach: Design networks with zero trust.
- Log everything: Full DNS, TLS, and HTTP/2 metadata.
- Integrate threat intel: Use feeds that track DGA, Fast Flux, and C2 domains.
- Train analysts: Teach them to spot high-entropy domains and JA3 anomalies.
- Update detection rules monthly: Evasion tactics evolve weekly.



I want to learn more about Fast Flux,
Single Flux, Double Flux, Domain Flux.
All about that technical or how to set it up with more details.
If you can help me about that, Thanks you so much.
We will explain more about this in future articles.