Do you know hackers don’t use online scanners for malware scanning and prefer crypter online scanner? Malicious creations of hackers, often operate in the shadows of cyberspace. They are employing sophisticated tools and techniques to evade detection and wreak havoc on unsuspecting victims.
One might assume that they would take advantage of online scanners, such as VirusTotal, for their malware scanning needs. However, the reality is quite the opposite and they are using FUD crypter scanner.
In this article, we’ll delve into the reasons why hackers steer clear of online scanners, especially when it comes to crypters and encrypted malware scanning.
The Risks of Using VirusTotal and Other Online Scanners for Encrypted Malware
Online scanners, touted as a panacea for detecting and eliminating malicious software, seem like the obvious choice for hackers seeking to test the efficacy of their creations.
However, the truth is far more nuanced. While these scanners offer convenience and accessibility, they come with significant drawbacks that deter seasoned cybercriminals.
#1. Risk of identification – lack of Stealth and Anonymity
Online scanners like VirusTotal, while invaluable tools for security researchers, pose a significant risk to hackers’ anonymity. These platforms often log and share information about submitted samples, including IP addresses and other metadata, which can potentially compromise their identities.
Moreover, the act of submitting malware samples to public platforms raises red flags and increases the likelihood of attracting unwanted attention from cybersecurity firms and law enforcement agencies. Hackers, driven by the desire to remain undetected, avoid such risks at all costs, opting for alternative methods that offer greater anonymity and control over their operations.
Operational security (OPSEC) is a critical aspect of hacking activities. Hackers go to great lengths to protect their identities, methods, and infrastructure from detection and disruption. Submitting malware samples to online scanners could potentially compromise their OPSEC by revealing valuable information about their tactics, techniques, and procedures (TTPs).
Security researchers and law enforcement agencies often analyze submitted samples to uncover patterns, attribution clues, and potential links to other cybercriminal activities. By avoiding online scanners, hackers can maintain a higher level of OPSEC, reducing the risk of exposing their operations and increasing their chances of remaining undetected.
#2. Instantly Improve Detection Rates and Stop FUD Results
In short, the effectiveness of shared FUD crypters depends on the behavior of all users. If anyone uploads a file to VirusTotal or other sample-distributing websites, it compromises the ability of others to get clean results. Conversely, a private STUB FUD crypter relies on just one user. However, regardless of whether a shared or private stub is uploaded to VirusTotal, users will lose FUD status. It destroyed malicious creations of hackers.
Why? VirusTotal flags your malware codes and modules, leading all antivirus programs to detect them. Note that the crypter only encrypts the payload and cannot alter the malware code, so it will be detected if the file is uploaded to VirusTotal.
First and foremost, online scanners raise the alarm bells of security organizations and antivirus companies. As soon as a malware sample is uploaded to platforms like VirusTotal, it undergoes rigorous scrutiny by an array of security engines.
This exposure increases the likelihood of the malware being cataloged and added to antivirus databases, rendering it useless for future attacks. For hackers, maintaining the element of surprise is paramount, and online scanners jeopardize that by tipping off the defenders.
Furthermore, online scanners often employ heuristics and signature-based detection techniques to identify malicious code. This means that even the slightest deviation from known malware patterns can trigger an alert. So, hackers use crypter online scanner instead.
Crypters, a staple tool in a hacker’s arsenal, are specifically designed to obfuscate and conceal malware, making it undetectable to traditional antivirus programs. By subjecting their creations to online scanners, hackers risk exposing the vulnerabilities of their crypters and compromising their effectiveness.
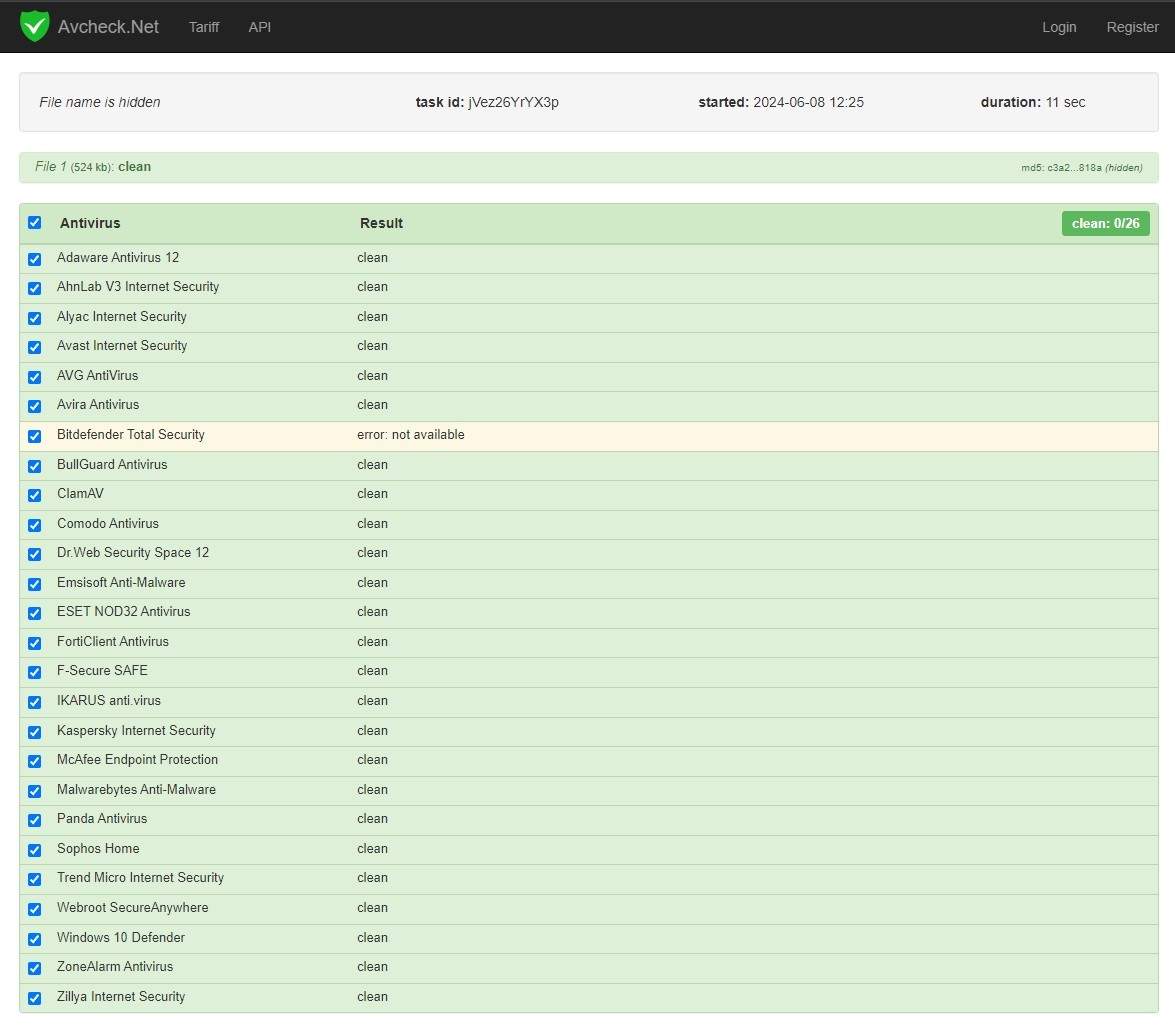
Hackers Scanner- Avcheck
Advanced Data and Statistics
To further illustrate the reasons behind hackers’ avoidance of online scanners like VirusTotal, it is essential to examine relevant data and statistics:
- Anonymity Concerns: According to a study by the Cyber Threat Alliance, over 60% of cybercriminals cited anonymity as their primary concern when considering the use of public malware analysis platforms. They use VMware platform for testing best RAT trojans 2022-2024 too.
- Detection Rates: Research conducted by the security firm Recorded Future revealed that the detection rates for newly developed malware samples on public online scanners can be as low as 20% within the first 24 hours of submission.
- Underground Market Dynamics: A report by Trend Micro highlighted that the exclusivity and scarcity of malware samples can increase their value on underground markets by up to 300%, incentivizing hackers to avoid public exposure.
- OPSEC Breaches: A case study by the FBI’s Cyber Division revealed that the analysis of a single malware sample submitted to a public online scanner led to the identification and disruption of a major cybercriminal operation, underscoring the importance of OPSEC for hackers.
- Private Malware Analysis Platforms: According to a survey by the cybersecurity firm Kaspersky, over 75% of hackers and cybercriminals rely on private malware analysis platforms within their trusted circles, citing privacy and control as the primary motivations.
- AVcheck Usage: Data from the AVcheck platform itself indicates a steady increase in user registrations and sample submissions, with a reported growth rate of over 30% annually, reflecting the demand for discreet malware analysis services among cybercriminals.
These statistics and data points highlight the significant concerns and motivations driving hackers’ avoidance of public online scanners like VirusTotal, reinforcing the importance of anonymity, exclusivity, and operational security in the world of cybercrime. Check Data Encoder Crypter blog for more details.
Crypter Online Scanner VS Malicious Creations Of Hackers
Enter the crypter online scanner, a battleground where hackers and security professionals engage in a perpetual game of cat and mouse. These specialized scanners are tailored to detect and analyze crypter-encrypted malware, posing a formidable challenge to cybercriminals.
Despite their efficacy, hackers remain wary of utilizing FUD crypter online scanners for several compelling reasons. Read more about step by step crypter works.
One primary concern is the inherent risk of exposure. Unlike traditional online scanners, crypter-specific platforms are designed to dissect the intricate layers of obfuscation employed by crypter online scanner.
This granular analysis not only reveals the underlying malware but also exposes the weaknesses of the crypter itself. For hackers, whose livelihoods depend on their ability to evade detection, such exposure is akin to handing their adversaries a roadmap to their illicit activities.
Moreover, malicious creations of hackers has spawned a thriving underground market for crypter detection evasion techniques. Hackers invest considerable time and resources into developing sophisticated crypters capable of bypassing even the most advanced online scanners.
By publicly testing their crypters on these platforms, they risk tipping off their competitors and inviting scrutiny from law enforcement agencies.
Online Scanners for Encrypted Malware Scanning: The Final Frontier
In the ever-evolving landscape of cybercrime, encrypted malware scanning represents the final frontier for hackers seeking to evade detection.
Unlike conventional malware, which relies on static signatures and behavioral analysis for detection, encrypted malware poses a unique challenge to security professionals.
Encryption, the process of encoding data to render it unreadable without the proper decryption key, adds an additional layer of complexity to malware scanning. By encrypting their malicious payloads, hackers can effectively conceal their activities from prying eyes, including online scanners and antivirus programs.
This cryptographic cloak not only thwarts detection but also complicates the analysis process, making it exceedingly difficult for security researchers to reverse engineer the malware. Also, crypter for ransomware use supplicated algorithms for avoid detections.
However, encrypted malware scanning is not without its limitations. While encryption may provide a temporary reprieve from detection, it is by no means foolproof. Security researchers are constantly devising innovative techniques to bypass encryption and uncover the secrets hidden within malicious creations of hackers.
From dynamic analysis and memory forensics to machine learning algorithms, the arsenal of tools at their disposal is vast and ever-expanding.
Exploring Malware Scanners: Leveraging Scantime and Runtime Analysis
Before delving into the intricacies of malware scanning, it’s essential to understand the distinction between scantime and runtime analysis. Scantime analysis occurs when a file is scanned before execution, typically during the download or initial access phase.
Runtime analysis, on the other hand, occurs during the execution of the malware, allowing for real-time monitoring of its behavior and actions. I short, we recommend Data Encoder crypter runtime checker or Runtime results ad compare with crypter online scanner.
For malicious creations of hackers, leveraging both scantime and runtime analysis offers a comprehensive approach. For evading detection and ensuring the success of their malicious campaigns. By understanding the strengths and limitations of each method, they can tailor their tactics accordingly to maximize their chances of success.
Scantime Scanner: Unveiling Vulnerabilities Before Execution
The scantime scanner serves as the first line of defense against malware, analyzing files before they are executed to identify potential threats. For hackers, this presents both an opportunity and a challenge. On one hand, scanning malware at scantime allows them to assess its detectability and make any necessary adjustments to evade detection. On the other hand, it exposes their creations to the scrutiny of security engines, increasing the risk of detection and cataloging.
To effectively leverage scantime scanning, hackers must adopt a proactive approach to evasion. This involves employing techniques such as polymorphism and code obfuscation to disguise the true nature of their malware. By constantly mutating their creations and obscuring their code, they can evade detection by traditional signature-based scanners and prolong the lifespan of their campaigns.
Furthermore, hackers can utilize online sandboxes and virtual environments to test the detectability of their malware in a controlled setting. By simulating the scanning behavior of security engines, they can identify potential vulnerabilities and fine-tune their evasion techniques accordingly. This iterative process of testing and refinement is crucial for staying one step ahead of defenders and maintaining the element of surprise. Check other hackers scanner with more details.
Runtime Scanner: Navigating the Dynamic Landscape of Execution
While scantime scanning provides valuable insights into the detectability of malware, runtime analysis offers a real-time view of its behavior and actions. For hackers, this presents a unique set of challenges and opportunities. On one hand, runtime crypter online scanner allows them to monitor the behavior of their malware and adapt to evolving detection techniques in real-time. On the other hand, it increases the risk of detection and remediation, as security solutions actively monitor and block malicious activities.
To effectively navigate the dynamic landscape of runtime scanning, hackers must employ evasion techniques that minimize their footprint and blend in with legitimate traffic. This may involve utilizing stealthy communication protocols, such as domain generation algorithms (DGAs) and peer-to-peer networks, to evade detection by network-based security solutions. Additionally, hackers can leverage anti-analysis techniques, such as sandbox evasion and code injection, to thwart dynamic analysis by security researchers.
Furthermore, hackers can leverage the power of machine learning and artificial intelligence to develop adaptive malware that can evade detection by runtime encrypted malware scanning. By training their creations on large datasets of benign and malicious samples, they can craft malware variants that are resilient to traditional detection techniques and capable of adapting to changing environments. This cat-and-mouse game between hackers and defenders underscores the importance of continuous innovation and adaptation in the field of cybersecurity.





Gusto Kong kumita