Best malware 2022 contaminated numerous systems and companies 2022 so download malware increased.
Mixed methods of cyber attacks and revamped hacking tools and malware have made it difficult to deal with them.
Therefore, in 2022, cyber security companies, antiviruses, and governments have concentrated on working jointly to deal with these attacks.
In this report, we decide to inform top malware 2022 based on the threats and ruin they have caused. Briefly, Data Encoder Crypter tries to analyze malware attacks in 2022 and compare the information and analyses with antivirus reports.
Top malware 2022 lists
We’ll take a close look at nine of the best malware available today:
- Redline – Best Stealer 2020-2022
- njRAT– Most in use remote access Trojans 2013-2022
- Formbook – leading Stealer 2016-2022
- WannaCry– Best Ransomware 2017-2022
- Agent Tesla– Best Keylogger for recording keystrokes 2014-2022
- Remcos – Updated RAT remote access trojans in 2016-2022
- Xloader– Top Botnet in 2020-2022
- Quasar RAT– Free RAT Trojan in 2015-2022
- Emotet– Advanced family of malware in 2014-2022
As you can see, we didn’t consider any exploits like zero-day exploits and silent exploits or vulnerabilities in this list.
Note some attackers use DNS tunneling for hiding IP and DNS.
Threats Analysis
Based on research, info stealer attacks raised 68% in 2022. Also, Stealer and RAT are the most hack tools that are sold in 2021-2022.
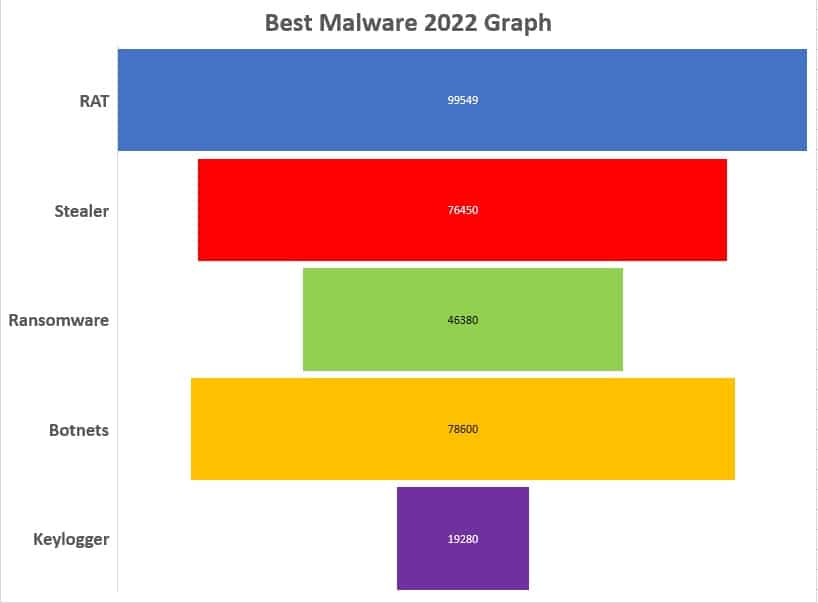
The best Stealer of the 2022 year is Redline, and the price starts from $150. Redline coder still provides updates and suggests her users buy malware crypter for bypassing antivirus.
Remote access trojans (RAT) have the largest share of the black market. The price of an updated RAT ranges from $37 to $600. For example, Remcos Pro is priced from $58 to $567.
But most hackers try to use free RAT, such as njRAT, Quasar, DcRAT, etc., for their daily tests. We have already prepared a list of the Best free RAT for crypter.
Crypter and Malware
As mentioned, the best malware 2022 regarding the last detection release the updates. The top malware such as Redline, Remcos, and Xloader are updating their product and compatible with crypter. Other free malware may be cracked and updated for Specific goals of a group. We recommend read more about what is a crypter. You can also find how make fud file with crypter.
All malware can’t bypass Windows Defender or another primary antivirus. For this, all coders suggest compatible crypter software. A fully undetectable FUD crypter encrypts the payload and injects it into legit windows processes. You can watch how make FUD njRAT and do the same for other malware and encrypts it with top malware packer.
The most important crypter options is clone assembly from app. Also, attackers use clone Code Sign certificate for longer FUD results. Read more about how crypter works.
Download and delivery it
If you want to download malware, it is so accessible with Telegram. Many coders are selling software with Telegram, Discord, and underground markets. In short, most malware delivery in 2025 is based on social networks or emails.
The last update of Google core help you for spreading malware or download it. Also, you can download it from Github too.
How will you infect with top malware?
You need to learn how a hacker may infect you.
- Social engineering.
- Email delivery.
- Google Ads.
- Downloading an unknown app or opening a link (Search engine links & emails)
- Free VPN
- Torrent Websites
- Social networks and etc.
Join our support bot for any issue.





Leave A Comment