A Crypter is encryption software to secure your data. Many hack tools such as malware, RAT, and ransomware try to access your information and need a payload crypter. We recommend encrypting your data with a crypter 2024. So this windows software encrypts your data, and you are the only person with an access key.
Do you want to stay against reverse engineering and hacker attacks with a crypting service?
In short, a safe encryption app is designed for encrypting any data. It will use pure cryptor code with process hollowing and PE Injection in simple ways.
A crypting service is a service that provides the ability to encrypt or scramble executable files to make them more challenging to analyze and detect by antivirus software. The purpose of using a crypting service is to conceal the true nature of a malicious executable, making it more difficult for antivirus software to identify it as malicious. The encrypted file can then be used for malicious purposes, such as distributing malware or conducting ai-generated deepfake ceo fraud, without being detected by antivirus software.
Cybercriminals frequently employ Crypting services to avoid detection by security software. Consequently, this makes it simpler to disseminate malware or initiate attacks. However, it’s crucial to recognize that while crypting services can enhance the difficulty of detecting malware, they do not assure complete invisibility. This is because security software is constantly advancing and adapting.
Malware crypter or Malware packer
Loads or malicious software are used to update malware on an infected computer. In short, Some load is generated by RAT remote access trojans.
The malware starts malicious processes. So launched Windows PowerShell with suspicious commands or encoded values. This was widespread malware last year.
Do you need to know how malware evades windows defender? Read our last post about payload crypter. You can watch the bypass antivirus videos too.
Also, the malware attempts to rename payloads to mimic system processes or replace them entirely. Malware Obfuscation inject it to Windows process by process hollowing and PE Injection method.
Hackers are using malware crypter 2025 to access data such as Stealer to access credentials hiddenly.
In short. RAT pc 2022-2025 has a hidden virtual network computing (HVNC) module. Watch how free RAT bypass Windows Defender.
RAT HVNC gives a robust management system that works hiddenly and uses a system process. Attackers use Clone Code Sign Certificate for HvNC payload crypter for longer FUD results.
The below page shows a Microsoft report showing the malware activity in May-June 2021.
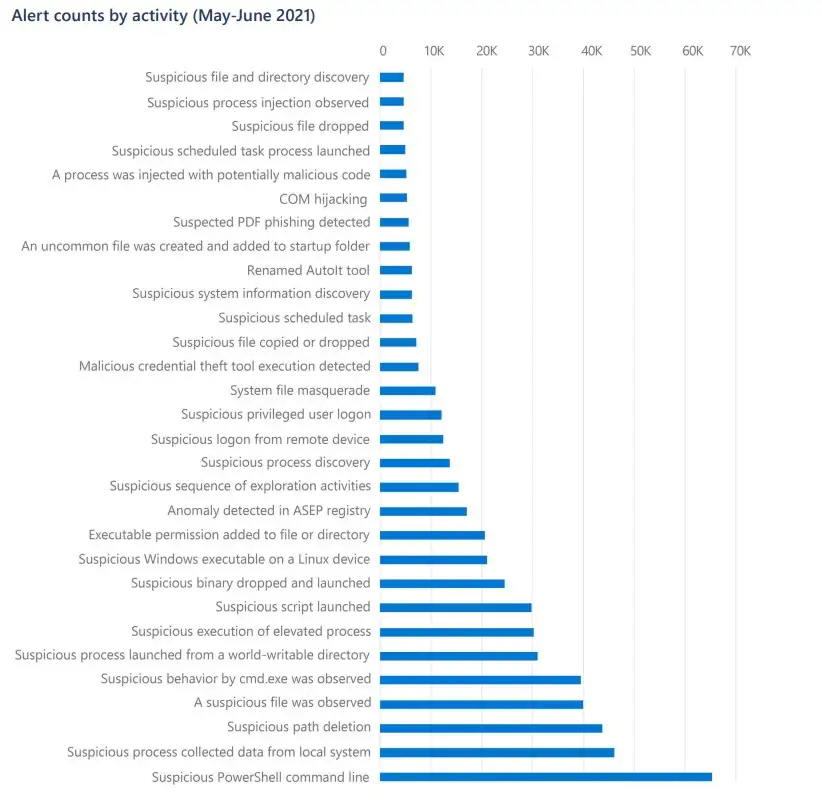
Briefly, malware make files hidden from user and security programs.
They are using the malware behavior but cannot bypass detection only. So professional users use best crypter 2025 to encrypt and obfuscate codes.
The victim, when clicking on the Malware exe, it decrypted by software and ran as a system process. Then malware remains fud exe. You can watch bypass false positive Windows Defender videos.
We recommend reading how to make my RAT FUD too. You can encrypt other malware to bypass primary antivirus if you discover how to make remote access trojans fully undetectable.
The bad news is that the coders are using the malware in the blockchain network. So many systems are controlling your systems and cannot find the attacker. Blockchain malware and payload crypter software make files fully undetectable FUD for a long time. We recommend reading our post when you start blogging; content the best miner 2021 too.
Crypter VS Ransomware
In this section, we will review the encrypting software vs ransomware.
A ransomware attack means deploying malware that encrypts like Qilin ransomware and exfiltrates data. The hacker holds sensitive data and encrypts it with a ransomware crypting service. The victim has to pay with cryptocurrency or a crypt token to the attacker to unencrypt the data. Some attackers use crypter binder option to laod more files with ransom payload. Malware packer make ransomware FUD from antivirus’s detections system with Fast Flux and DNS Tunneling.
But the crypting software windows help you secure data against any ransomware. So you can crypting your data before any ransomware. Then the ransomware cannot request a ransom in exchange for the decryption key.
Big game ransomware or human ransom is increasing in 2025, and the top malware in 2025 is ransomware and Stealer.
We strongly recommend creating a taxonomy from your data and encrypting it with different cryptography algorithms.
The core goal of cryptography is to have all your data safe in one place, right?
You can crypt your files and bind others with payload encryption tool or other typs of crypting service (including exe, office, APK, etc.)
So you can easily decrypt them and get connection.
Just download it and secure your data.
Do you need a free crypter? Just read about the advantages and disadvantages of free tools.
There’s even more on top of that, believe me.
Distributing the FUD Malware
To infect systems, hackers need to distribute the FUD malware. This can be done through various methods, such as:
- Phishing emails with malicious attachments or links
- Compromised websites hosting the malware
- Exploiting software vulnerabilities to deliver the payload
- Social engineering tactics to trick users into running the malware
FUD malware poses a significant threat to organizations and individuals alike. By understanding how hackers create and distribute these threats, security professionals and red teams can better prepare and defend against them. Regular updates, user education, and the adoption of advanced security solutions are crucial in mitigating the risks posed by FUD malware.
So why aren’t you using it?
I guess it’s because the price is high for low volume data and challenging to use.
That was true, but not anymore.
We are sure you can use it at a user-friendly and low price, such as Data Encoder Crypter.
They’re affordable, sleek, and ready to help teams connect with customers on our terms.
On top of that, you get unlimited crypt, and it’s free forever, so you don’t have to worry about how many encrypts you make while trying to grow.
Briefly, the payload crypter stub generates pure code to encrypt your data. Note data encoding software just encrypts the codes and inject them.
Also, you can buy a private package if your data is more sensitive and need safe encryption with Private STUB.
Crypting price
Here’s The Best crypter Software for 2024 to secure your data to the next level. Watch the encryption tutorials for more information,
#1. Data Encoder Review
If you want to keep more safe, Data Encoder is the software you’ve been looking for.
It’s a great way to take your encrypting process to the next level.
It’s also one of the more affordable options on the market, starting at just $60 per 45 days per user. Even at the private package, it’s cheap at just $450 per user with unlimited crypt.
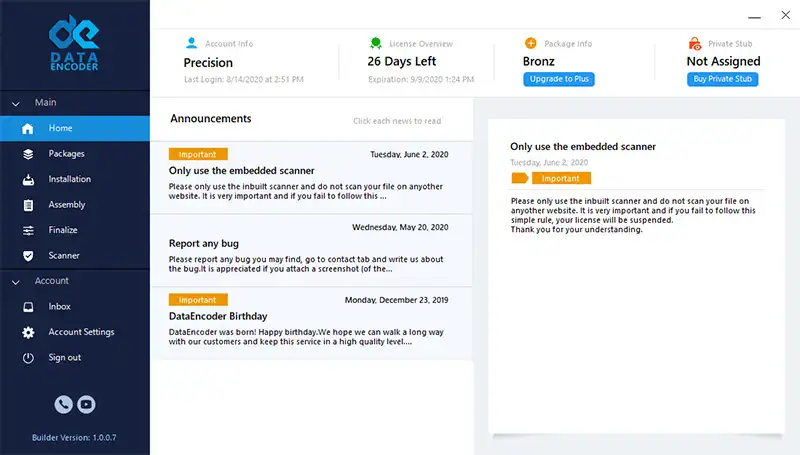
So, how does the software work? Data Encoder software uses a simple setup, so it’s easy to see where leads are in the process. It’s also customizable, so you can drag and drop your files and add custom fields to build a tool that works with your current methods.
Here’s a look at what your main dashboard could look like (Keep in mind, you can customize it):
Conclusion:
We started blogging more than 4 years ago.
Our business has a lot of moving parts now. Thousands of customers’ data encrypt every hour with our crypter software.
If you are looking for a data security solution against Ransomware, silent exploit, zero-day exploit, Rat remote access trojans 2022, and Loader malware, botnets, Data Encoder is the best choice for all.

